February 15, 2018
How to Secure Domain Controllers with Next-Gen Firewalls

One of the principal ways to increase the security of your network is using smaller subnetworks called network segments. This process also improves network performance typically. This is done by limiting the privileges and access of users and applications between elements in the environment. These practices help to limit undesirable activity, access and movement across the network by reducing the ability of a malicious entity to pivot within the environment. Segmentation helps to prevent attacks and keep them from spreading when they do occur.
In today’s post, we provide specific examples of how to implement these policies within a Palo Alto Networks firewall. It’s important to note the same general policies can apply to virtually any firewall. We also take special note of the features of a next-gen firewall, particularly the ability to identify traffic based on the application used and not just the port in question.
Why secure domain controllers?
An Active Directory Domain Controller (DC) is a server that manages several crucial tasks within an Active Directory environment. Domain controllers are essential parts of the Windows Active Directory service. They authenticate users, store user account information and enforce security policy for an Active Directory domain. In many environments, compromising a privileged Active Directory account, like a domain admin, can lead to the compromise of all systems within an enterprise. Ensuring DCs remain secure is crucial to maintaining a safe infrastructure.
What impact does segmentation have on domain controllers?
One goal of network segmentation of domain controllers is to prevent attackers from gaining access to critical systems by exploiting unrestricted and unnecessary services. This will reduce the risk of compromise that arises from unauthorized access to unused or unnecessary features and services. While there are many methods to execute this practice, the most successful for organizations is to restrict access at the network level and ensure that unauthorized personal are unable to even make connections to services that should not be used.
Step 1: Policy Creation
Policy creation is critical to properly securing any domain controller. In particular, whitelisting of all allowed applications and services creates a more secure environment and prevents exploitation by attackers. Creating an explicit, deny-all policy to prevent undesirable use of and movement across your network is what ensures a firewall is functioning in a whitelist method, instead of a blacklist method.
While most firewalls have an implicit deny-all, some do not. For instance, Palo Alto firewalls have two implicit rules: one that allows all traffic within the same zone (trust to trust, etc) and one that denies all traffic from one zone to another. Another benefit of an explicit deny-all is Palo Alto firewalls do not log traffic that hits these rules by default. This deny explicit rule helps in controlling and monitoring activity within the network.
The explicit deny-all rule is often defined as follows:

This Deny-All rule should be the last on the list of policies, as any rules that are lower on the list will never be evaluated. This is known as a rule “shadowing” another.
Step 2: Leverage Palo Alto Networks App-ID
Leveraging Palo Alto’s App-ID feature, you can identify applications on a specified network. With App-ID, Palo Alto is able to find and deny traffic from unwanted sources while still allowing traffic from desired sources, even if they use the same port. App-ID works by analyzing and understanding the contextual signatures that comes from the traffic that traverses through the firewall. Once enough information is obtained, the App-ID feature can determine what the application is and what protocol is being used.
Step 3: Whitelist Essential Application Services
Next, you will want to whitelist services that are essential to your domain controller’s standard functions. This guide provides the UDP and TCP ports used, as well as the names of the applications as they are designated by Palo Alto’s App-ID feature. These details should be used to create policies within the firewall to allow access. The sources of this traffic should be those subnets authorized to access these services.
Active Directory
Active Directory (AD) is a directory service for Windows domain networks that is primarily a set of processes and services. Domain controllers run Active Directory Domain Service (AD DS) in order to authenticate and authorize users and computers.
TCP Ports: 1025-5000, 135, 138, 139, 389, 445, 464, 636, 49152-65535, 5722, 9389
UDP Ports: 88, 123, 137, 138, 389, 445, 464, 2535
DNS:
Domain Name System (DNS) is a system of translating domain names into IP addresses used for navigating to and around web pages. DNS acts as a directory service and is critical to any network system.
TCP Ports: 53
UDP Ports: 53, 5353
NTP
Network Time Protocol (NTP) is a networking protocol that is used for clock synchronization between computer systems over variable-latency, packet-switched data networks. NTP attempts to synchronize all computers participating in a network action.
TCP Ports: 123
UDP Ports: 123
Kerberos
Kerberos is a computer network authentication protocol used by most operating systems to allow communication between nodes to have secure identity verification. Kerberos works by sending authentication tickets to a service that, in turn, verifies the client to other nodes for communication.
TCP Ports: 88, 464, 749, 750
UDP Ports: 88, 464, 749, 750
NetBIOS-NS
Network Basic Input/Output System (NetBIOS) provides services that are related to the session layer of the OSI model which allows applications on separate computers to communicate over a local area network (LAN). Name Service (NS) is used for the registration and management of application’s NetBIOS names.
TCP Ports: 137
UDP Ports: 137
NetBIOS-SS
NetBIOS also has a service named Session Service, a mode that lets two computers establish a connection, allows for messages to span over multiple packets, and provides error detection and recovery.
TCP Ports: 139
NetBIOS-DG
The last part of NetBIOS is called Datagram Distribution service, also referred to as Datagram mode. This mode is connectionless and is responsible for sending and receiving datagrams.
UDP Ports: 138
MSRPC
Microsoft Remote Procedure Call (MSRPC) is a modified version of Distributed Computing Environment / Remote Procedure Calls (DCE/RPC), which allows for distributed software to be written as if it were on the same computer, ignoring underlying network code.
TCP Ports: 593, dynamic
UDP Ports: 88, dynamic
LDAP
Lightweight Directory Access Protocol (LDAP) is an industry standard application protocol used for accessing and maintaining distributed directory information services over an IP network.
TCP Ports: 389, 3268, 3269, 636
UDP Ports: 389, 3268
MS-NetLogon
NetLogon is a service which verifies NTLM logon requests and registers, authenticates, and locates domain controllers. NetLogon also manages replication of the user account database to back up domain controllers running Windows NT 4.0 and earlier.
TCP Ports: 135, 139, 445, 1025-5000, 49152-65535
UDP Ports: 137, 138, 445
MS-DS-SMB
Server Message Block (SMB) is an application-layer network protocol that is primarily used to give shared access to files, printer, ports, and communications between network nodes. Microsoft took SMB and added security protocols and other extension to its own implementation.
TCP Ports: 139, 445
UDP Ports: 445
Windows-Remote-Management
Windows Remote Management (WinRM) is the Microsoft implementation of WS-Management Protocol, a standard Simple Object Access Protocol (SOAP)-based, firewall-friendly protocol that allows hardware and operating systems, from different vendors, to operate with each other.
TDP Ports: 5985, 5986
Step 4: Whitelist Optional, Non- Essential Application Services
Next, you will want to whitelist optional and non-essential applications services that are essential to your domain controllers.
MS-RDP
Remote Desktop Protocol (RDP) was developed by Microsoft to provide users with a graphical interface with which to connect to another computer over a network. For a domain controller, you only need RDP usage for users in the admin group.
TCP Ports: 3389
UDP Ports: 3389
Print-Over-MS-SMB
This protocol identifies printer traffic that uses server message block. MSRPC and MS-DS-SMB must be enabled for this application to work. This is only necessary if there is printer traffic going into the domain controller.
TCP Ports: dynamic
RADIUS
Remote Authentication Dial In User Service (RADIUS) is an AAA (authentication, authorization, and accounting) protocol for network access or IP mobility. Only enable this application service if the domain controller(s) also hosts a RADIUS server.
UDP Ports: 1813, 1812, 1645, 1646
Ping
Ping is a computer network administration software utility used in testing the reachability of a host on an Internet Protocol (IP) network. To do so, it measures the time it takes for a series of packets to go from origin to destination and back. Only enable this application service when you need to troubleshoot.
Protocol: ICMP
Step 5: Generate Your Security Policy
Next, generate your Security Policy for your network. Here is an example.
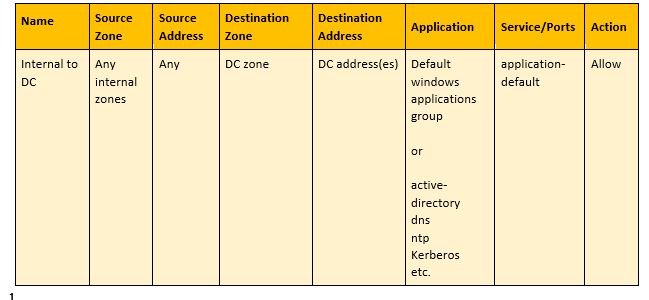
Source Zone:
Name:
The name of the Security Policy.
The zone in which the systems that need to communicate to the Domain Controller(s) reside.
Source Address:
The address of the source zone.
Destination Zone:
The zone that contains the Domain Controller(s).
Destination Address:
The IP address or defined address of the Domain Controllers.
Application:
The defined application group or the listed applications listed above.
Service/Ports:
Depending on the Action, Application-default forces the application to use its default specified port(s). This, in return, prevents application from being exploited to run on unusual ports and protocol. If Any is selected, then any ports can be used as long as Palo Alto identifies the application that is running on those port(s) as part of the allowed applications.
Action:
This determines what the firewall will do if a traffic matches the security policy.
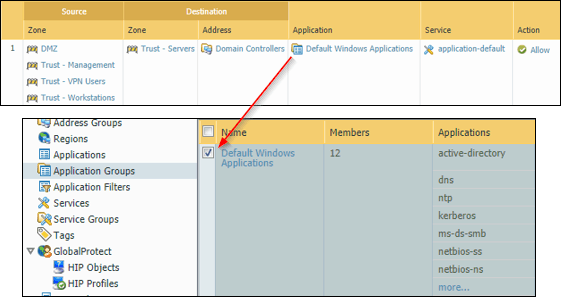
Figure 1 – Example of a Secured Domain Controller(s) Policy
Using Other Enterprise Level Firewalls
Whitelisting is not a proprietary strategy to only Palo Alto. Many enterprise level firewalls allow you to whitelist services and applications for secure usage. Although many legacy firewalls lack the capability of Palo Alto’s App-ID, you can secure a domain controller by only allowing known ports as mentioned earlier to communicate with and access your domain controllers.
Other next-gen firewalls that offer similar capabilities to Palo Alto’s App-ID include ForcePoint, FortiNet, Sophos, Juniper, and Check Point. You can secure your domain Controllers using these firewalls following similar procedures as we mentioned in this guide.
About the Authors
Ben Dimick is an information security manager at Tevora.
Tin Nguyen and Brandon Richardson are information security associates at Tevora.