July 30, 2021
HydraRisk Model—A New Approach to Risk Assessments
Tevora’s HydraRisk Model offers a unique approach to assessing enterprise risks that is easy to implement and tailored to your environment. It uses a balanced combination of quantitative and qualitative factors for identifying and prioritizing risks, enabling you to raise your organization’s risk management maturity to the next level.
In this blog post, we’ll describe our innovative HydraRisk approach and compare it with other commonly-used risk assessment models.
Key Terms
First, let’s define a few important terms.
- Asset: A valuable tangible or intangible item worth protecting. Tangible assets can be things such as laptops, servers, or credit card transaction data. Reputation and intellectual property are examples of intangible assets.
- Threat: Anything within an environment that can act towards an asset. Threats can be malicious or non-malicious. Cybercriminals pose malicious threats. An employee accidentally typing in a wrong code or disclosing sensitive information is a non-malicious threat.
- Vulnerabilities: Weaknesses in the design, implementation, operation, or monitoring of a control. Examples include using shared passwords, leaving sensitive data exposed to threats, and weak authentication/authorization. Having proper controls in place can mitigate or eliminate vulnerabilities.
- Risk: The exploitation of a vulnerability by a threat on an asset that impacts an organization. Inherent risks are the risks associated with a specific asset before any security controls are put in place. Residual risks are the risks that remain after security controls are implemented.
Common Themes in Risk Assessment Frameworks
Most organizations use some form of risk assessment framework to identify and mitigate organizational risks. These frameworks typically share the following general process steps and themes:
Lifecycle of Risk
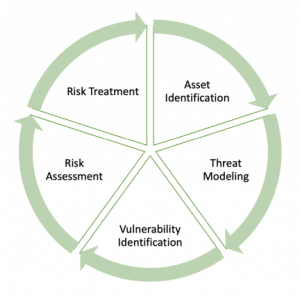
- Asset Identification
- Threat Modeling
- Vulnerability Identification
- Risk Assessment
- Risk Treatment:
Risk Assessment Models
There are many ways organizations assess risks from a cybersecurity perspective. Some mainly rely on statistical models and metrics. Others focus more on qualitative methods. In this section, we’ll cover some of the most common risk assessment models we see in our work with clients and highlight the benefits and drawbacks of each model.
Factor Analysis of Information Risk (FAIR):
FAIR is a highly quantitative model that takes a deep dive into factors that impact specific threat scenarios. Each identified scenario is assigned a quantitative value for the frequency with which loss events occur and the magnitude of the loss for each loss event. These metrics are used to assign a financial value to the expected annualized losses associated with each loss scenario.
- Benefits:
- Deep quantitative analysis removes subjectivity.
- Provides metrics to prioritize risks and justify implementation of controls to mitigate risks.
- Heavily focused on security.
- Drawbacks:
- Time consuming process.
- Requires operational data.
- Requires significant amount of dedicated, highly-skilled resources (e.g., Monte Carlo simulation expertise is needed).
- Not the best choice for organizations that are new to risk assessment.
Operationally Critical Threat, Asset and Vulnerability Evaluation (OCTAVE)
OCTAVE is a more qualitative risk assessment approach that uses an eight-step process to identify and document specific threats, assets, and vulnerabilities for an organization. The process relies on workshops to gather qualitative information on the organization’s perceived risks. It also provides many worksheets which guide users in providing information on threats, assets, vulnerabilities, and risks.
Risks are assigned a qualitative rating of “High,” “Medium,” or “Low,” which each correlate to a numerical score value. Priorities for implementing mitigating controls are based on the combined score for each risk.
- Benefits:
- Foundational risk assessment process, which covers the basics of risk.
- Simpler to conduct. Abundance of guidance in form of worksheets and process documentation.
- Does not require expertise and resources to conduct complex quantitative analysis.
- Well-suited to organizations that are just beginning to use a risk assessment process.
- Drawbacks:
- Time consuming to complete all documentation, workshops, and other tasks associated with the eight-step process.
- Lack of security focus. Does not include detailed analysis of security threat scenarios.
- Lack of quantitative analysis and metrics can make it more difficult to justify expenditures to mitigate identified risks.
NIST 800-30 – Guide for Conducting Risk Assessments
The NIST-800-30 Guide was published by the U.S. government to be used for risk assessments of federal and state assets. Tevora has incorporated many elements from NIST-800-30 in its HydraRisk model.
HydraRisk Model
HydraRisk is a proprietary quantitative and qualitative hybrid risk model developed by Tevora. While it draws from NIST 800-30 and NIST CSF, many aspects of the model are based on lessons learned from Tevora’s extensive work with clients to help them implement risk models.
Tevora’s model takes the best of the FAIR, OCTAVE, and NIST-800-30 models to help organizations effectively assess strategic and security risks. HydraRisk accomplishes this without requiring deep statistical resources and requirements. However, it does provide more quantitative metrics than a purely qualitative model. These quantitative metrics provide organizations with strong justification for expenses required to mitigate identified risks.
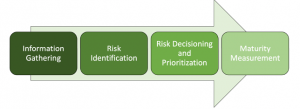
The four steps of the HydraRisk process are summarized below.
HydraRisk Process
Information Gathering
- Review applicable laws and requirements and the organization’s mission and objectives to determine what’s most important to the business.
- Review current processes and technical controls and identify gaps and areas for improvement.
- Review current documentation, including policies, standards, and procedures. Determine if there are any documentation gaps. Determine if documentation is being properly distributed to employees.
- Conduct guided observation of systems and technical processes to determine if documented processes are being properly executed in organization’s environment.
Risk Identification
- Conduct formal, informal, and informational interviews to identify opportunities for vulnerabilities to be exploited and treatment processes that should be implemented in the information security risk program.
- Use NIST CSF Framework of “Identify, Prevent, Detect, Respond, and Recover” to assess where security controls are missing or inadequate.
Risk Decisioning and Prioritization
- Use the five-factor HydraRisk Assessment Scoring Scale to assign weighted scores to identified risks. The factors are:
- Use the scoring matrix below to assign risk scores ranging from 1 – 5 for each identified risk:
HydraRisk Assessment Scoring
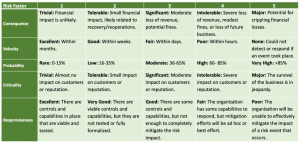
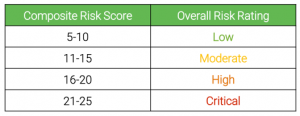
- Combine the five risk scores to generate a composite risk score for each identified risk, which gives an overall indication of the severity of the risk. The table below shows the ranges used for assigning overall risk ratings.
- The HydraRisk scoring methodology provides a consistent way to measure, compare, and prioritize risks across an organization.
Maturity Measurement
- As organizations enhance their information security controls in response to identified risks, they can use the Hydra scoring system to periodically reassess risks. This provides a quantitative method for measuring their progress in maturing risk management capabilities.
Why HydraRisk?
To wrap this up, here’s our take on why you should use HydraRisk:
- It’s a tailored, simple approach. The five metrics make it easy and cost-effective for businesses to assess cyber risk without needing to perform expensive, time-consuming, and resource-intensive quantitative analysis.
- It uses a balanced approach to evaluating risks, combining qualitative and quantitative factors.
- Enables program maturity by identifying, prioritizing, and justifying enhancements to security controls that propel your organization to higher levels of risk management maturity.
Webinar
For a deeper dive on these topics, check out Tevora’s webinar covering HydraRisk and other cybersecurity risk models.
We Can Help
If you have questions about the HydraRisk Model or would like help using it in your environment, our team of enterprise risk specialists can help. We have used HydraRisk to perform security risk assessments for some of the world’s leading organizations and would welcome the chance to do this for you.
To learn more about how we can help, just give us a call at (833) 292-1609 or email us at sales@tevora.com.
About the Author
Luke Mueller is an Information Security Analyst at Tevora.