July 9, 2021
Use the OWASP Top 10 Privacy Risks To Ensure Rock-Solid Privacy in Your Web Applications
The Open Web Application Security Project® (OWASP) Foundation works to improve the security of software through community-led open-source software projects.
The OWASP Top 10 Privacy Risks Project provides a top 10 list for privacy risks in web applications, including countermeasures for each risk. It also provides tips on implementing privacy by design in web applications to help developers and web application providers better understand and improve privacy.
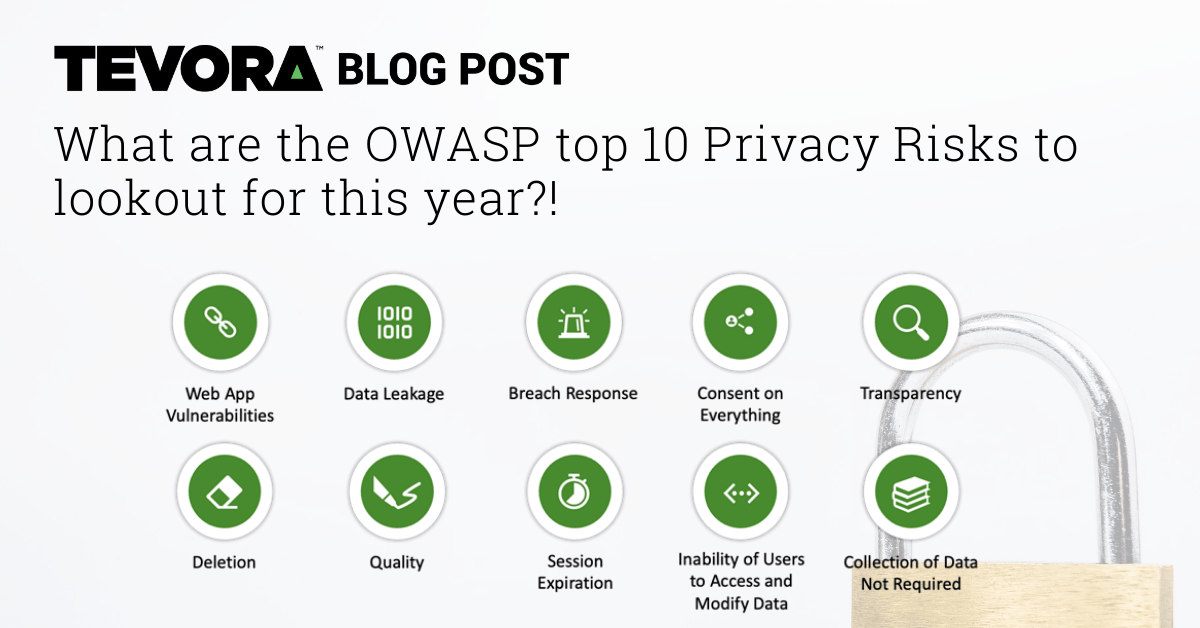
OWASP has recently released Version 2.0 of its Top 10 Privacy Risks, which is the version we’ll be discussing. Here’s a summary of the Version 2.0 risks:
OWASP Top 10 Privacy Risks
In this blog post, we’ll review the OWASP Version 2.0 risks, important considerations, and actions you can take to mitigate each risk.
1. Web Application Vulnerabilities
This risk encompasses all of the following OWASP Top 10 Web Application Security Risks:
- Injection
- Broken Authentication
- Sensitive Data Exposure
- External Entities (XXE)
- Broken Access Control
- Security Misconfiguration
- Cross Site Scripting (XSS)
- Insecure Deserialization
- Using Components with Known Vulnerabilities
- Insufficient Logging and Monitoring
Considerations
We recommend incorporating considerations for each of these risks in your web application development cycle. Based on our experience working with clients, some of the most important vulnerabilities to look for in your web applications are sensitive data exposure, broken access controls, and insufficient logging and monitoring.
Avoiding Excessive Web Application Vulnerabilities
Web application vulnerability management requires both formal planning and continued monitoring and testing. Avoid vulnerabilities and data exposure with proactive management.
- Effective vulnerability management requires formal planning and accountability. Develop detailed documentation on what you will be testing and how.
- Test applications at scheduled intervals. Perform internal and external testing. Ensure critical systems are kept updated. Seek independent critique.
- Secure Development. Ingrain security and privacy throughout the development process. Test code thoroughly. Ensure staff and outside parties are aware of secure coding principles.
2. Data Leakage
This is the risk that your sensitive information can be accessed or exported without authorization.
Considerations
What opportunities exist for your personal information to be accessed by cyber attackers?
Information traverses many systems throughout its lifecycle. Has each system and endpoint been locked down to avoid leaks?
Is access to your company’s resources limited to only those users that have a legitimate need to access them?
How are employees sharing personal information?
Preventing Data Leakage
- Understand where your data exists across all platforms. Collect the least possible amount of information to shrink the risk surface. Implement automated scrubbing, de-identification, anonymization, and encryption of personal information.
- Limiting Access. Minimizing access minimizes risk. Ensure access is controlled at high levels. Use groups were possible. Continuously review and update access privileges to adapt to changing business conditions and personnel responsibilities. Monitor and log all requests for access. Above all else, be wary of access by third parties, vendors, business partners, and any other outside parties.
- People need to share data. It is important to provide them with secure means to do so and to ensure they know the correct sharing protocols. Conduct employee training on personal information sharing.
3. Breach Response
This is the risk that you are not adequately prepared to quickly contain a breach and notify affected parties.
Considerations
If you are breached, will you be able to understand which levels of personal information have been breached?
Has your valuable information been protected with minimization, anonymization, and encryption?
Do you have adequate monitoring and logging in place to understand what is occurring during a breach?
Do your incident response plans incorporate data protection regulatory requirements? Do they include specific timelines for incident response activities? Do they include plans for notifying and working with third parties to remediate damages?
Managing Breaches from a Privacy Perspective
Take your incident response process a step further by ensuring privacy requirements are met.
- Always Understand. To understand the breadth of impact to personal information and how to respond, you should know exactly what information is on each system. This requires proactive analysis.
- If your information set is small due to auto-purging and de-identified information, both its value to attackers and overall breach repercussions are diminished.
- Plan Ahead. Update existing incident response plans to reflect specific privacy requirements such as who to notify, timelines, and fines. In this instance, be granular.
4. Consent On Everything
The risk that an organization may knowingly or unknowingly be handling personal information outside of the bounds of the original purpose of collection. This can include unauthorized sharing and aggregation of information for analytics.
Considerations
Have you identified the consent requirements your organization faces?
Have you documented a consent management policy?
How do you manage consent?
Do you know how personal information is being shared internally or with other parties?
Centrally Manage Consent
Take these steps to work towards central consent management:
- Perform an analysis of which regulatory requirements for consent are in place.
- Document these requirements with data governance activities.
- Develop consent runbooks for your organization; identify the specific scenarios in which personal data is collected and determine how consent will be collected.
- Centrally manage consent for data subjects.
5. Transparency
This is the risk that a company is not adequately transparent in explaining how their customers’ information is collected, stored, and used.
Considerations
Are you developing a PIA for all new processes?
Do you have a good understanding of what data is needed, for what purpose, and for how long?
What information, if any, will be shared with external parties?
Are you capturing and sharing information as needed to satisfy California Privacy Rights Act (CPRA) requirements?
Implement Transparency to Support Compliance Requirements
Transparent data use requires internal compliance with privacy regulations, which is beneficial for organizations.
- Maintain transparency by documenting the types of information needed, why it is needed, and who it will be shared with. Does your staff understand acceptable use? If not, conduct training to ensure they do.
- Information governance should consider compliance requirements. Ensuring all provisions can be met requires transparency.
- Third-Party Compliance. The purpose of processing is a major component in ensuring transparency. Managing vendors from the highest level ensures data sharing is understood fully.
6. Deletion
This is the risk that information is vulnerable to compromise because an organization fails to purge unneeded information from its environment.
Considerations
Have you documented the data lifecycle from start to end?
Is all of the data you have necessary?
Have you defined the right regulatory steps for data deletion?
Where can you automate the data deletion process?
Do you understand the full residency of personal information?
What are your staff’s responsibilities for data deletion?
Secure Data at the End of its Lifecycle
Prevent excessive leakage by purging data at the end of its lifecycle.
- Specific Purpose. Every new process needs a Privacy Impact Assessment (PIA). This is where the data lifecycle should be defined. Once your privacy notice is built, stick to it.
- Information governance is its own function, necessary for clean deletion in your environment. Documentation should include staff and other environments.
- Take advantage of native tools and scripts to purge datastores based on the age of the data or other parameters.
7. Quality
This is the risk that inaccuracies in the data you collect and use will result in failure to adequately protect personal information and comply with data privacy and security standards.
Considerations
Is content user-submitted? Are sources accurate? Has older data become inaccurate?
Is accuracy built into your processes? What kind of data accuracy health checks are you doing (e.g., PIAs)?
Ensuring Accuracy
Ensuring data accuracy helps you protect the data subject, comply with data privacy and security standards, and make the best use of information sets.
- Add accuracy checks in your information governance program and set goals. Purges, manual reviews, and source checks all help ensure accuracy.
- Data inventories based on full scans give a much simpler look into all datastores. Take advantage of this to set purging and accuracy goals.
- For data being pulled from multiple sources, use scripting and hash functions to verity data integrity and remove unneeded data.
8. Session Expiration
This is the risk that failure to terminate sessions after periods of inactivity will leave systems vulnerable to attack.
Considerations
Are users being authenticated securely?
Are you enforcing timeouts?
Do users know they need to log out?
Implement Systems and Training to Ensure Secure Session Expiration
- Automate Lockout. Configure applications and remote connections to disconnect after specific periods of time. Try to make them as short as possible to minimize potential attack windows.
- While users may prefer to remain logged in to avoid tedious re-authentication, it’s important to educate them about why this is a bad practice. Consider use of a single sign-on tool.
9. Inability of Users to Access and Modify Data
This risk entails the inability of users to change, access, or delete their personal information.
Considerations
Do we know where all of our user information is?
Have we defined data subject requests?
Can we make the data user accessible?
Ensure Users Can Access and Modify Data
Succinct data inventorying is key to ensuring staff can access or modify their information. If data is properly mapped and linkable, then users can access their information either through self-service portals with the right tools or through the organization by submitting a subject request.
In managing requests, be sure:
- Requests are formally documented.
- Public websites have links for submitting data subject requests.
10. Collection of Data Not Required
This is the risk that data will be used improperly beyond the correct purposes of collection.
Considerations
Have you documented the purpose of data usage and communicated it to all users?
Have you created a corporate culture of collecting the minimum amount of personal information required to perform required business functions?
Are you providing data subjects the right to opt-out at the time of data collection?
Are you compliant with applicable regulations regarding obtaining consent from data subjects?
Are you adequately anonymizing personal information?
Only Use Information for Specific Purposes
Ensure that you only use personal information for specific business purposes.
- Access and Permission. Establish barriers to entry for information to limit the potential for unwarranted use. Require formal approval for all new processing activities. Ensure all connections are secure.
- For analytics, research, and other purposes, use anonymized information. Dedicated tools make this easier and lower the risk of de-identification.
Tevora Webinar
For a deeper dive into OWASP Top 10 Security Risks, check out the recording of Tevora’s recent webinar on this topic.
We Can Help
If you have questions about the OWASP Top 10 Security Risks or would like help mitigating these risks in your web applications, Tevora’s team of security specialists can help. Just give us a call at (833) 292-1609 or email us at sales@tevora.com.
About the Author
Adoriel Bethishou is a Senior Information Security Analyst at Tevora.