The Benefits of Certifying for ISO 27701?
With data privacy concerns getting prominent play in so many headlines recently, you may be trying to decide whether to seek certification for the ISO 27701 privacy standard. If so, you’ve come to the right place! In this blog post, we’ll explain what the standard is, how it differs from ISO 27001, what benefits certification will provide, and steps you should take to get started on the road to ISO 27701 certification.
What Is ISO 27701?
The International Organization for Standards (ISO) 27701 standard provides requirements and guidance for establishing, implementing, and continually improving a Privacy Information Management System (PIMS). ISO defines a PIMS as an “information security management system, which addresses the protection of privacy as potentially affected by the processing of Personally Identifiable Information (PII).”
ISO 27701 is an extension of 27001, which guides organizations in managing information security. ISO 27701 builds on 27001 guidance and requirements with respect to the management of PII.
The scope of ISO 27701 includes:
- Everything in 27001, plus extended guidance and requirements for managing PII, including data processing activities and supporting processes.
- Guidance for determining if you are a “PII controller” (including being part of a joint PII controller) and/or a “PII processor”; provides requirements for each.
- Identification of applicable:
- Regulations.
- Organizational context and privacy goals.
- Contract requirements.
- Industry requirements.
- Requirement that organizations appoint an independent individual(s) to ensure compliance and act as an expert(s) in privacy compliance.
- Requirement that organizations ensure that their customers meeting any of the definitions below are also compliant with 27701.
- Organization contracted with PII Controller.
- PII Controller contracted with PII Processor.
- PII Processor contracted with subcontractor.
- Requirement that an organization’s PIMS is comprised of:
- Designated privacy management team.
- Well-trained staff.
- Information mapping and processing documentation.
- Specific privacy policies, procedures, and organizational functions.
- Privacy technology.
We suggest that you consider implementation of ISO 27701 as an extension of the requirements for an Information Security Management System (ISMS) that are included in ISO 27001. You’ll want to perform the same types of activities you would use for an ISMS, including:
- Identify stakeholders.
- Determine goals, timelines, and costs.
- Document roles.
- Determine total scope (consult all business units).
- Document PIMS, including key policies, procedures, support functions, ISO audit cycle, and operations.
- Document privacy risk management process. Can be a stand-alone process or integrated with your security risk management process.
What Are the Key Differences Between ISO 27001 and 27701?
Here’s a summary of the key differences between ISO 27001 and 27701:
- ISMS vs. PIMS.
- ISO 27001 defines requirements for an Information Security Management System (ISMS), which focuses on managing an organization’s security to protect critical assets and operations. The ISMS is designed to create accountability for security of the organization and to establish oversight.
- ISO 27701 defines requirements for an organization’s Privacy Information Management System (PIMS). The PIMS should be viewed as an extension to your ISMS. Many of the key elements of the ISMS will be replicated in the PIMS. As policies and procedures for 27701 are drafted, you will find that many requirements are met by extending 27001 controls.
- Expanded Security Requirements for Data Protection.
- ISO 27701 expands 27001 security requirements to include data protection principles and requirements. Organizations can use baselines established for 27001 to build 27701 policies, procedures, and implementation technologies. Here are some of the key areas of expanded requirements:
- Human Resources Security – Targeted privacy training for relevant staff involved in PII processing.
- Asset Management – Integration of PII as part of the asset classification scheme; additional requirements for media.
- Access Control – Record of users accessing PII; secure log-on for customers.
- Cryptography – Disclosure to customers of encryption standards and the ability to apply their own; encryption in transit.
- Retention and Disposal – Explicit requirements for deletion and re-use of storage; restriction of hardcopy PII use.
- Backup – Policies to address PII backup, erasure, disclosure and transparency to customers, and integrity and logging of PII during restores.
- Logging – Consider how PII may be in logs and how it is erased.
- Development – Privacy by design and default and restriction of PII usage.
- Suppliers – Requirements for ensuring the same standards of PII protection downstream and in contracts.
While it’s beyond the scope of this blog post, it’s worth mentioning that the ISO 27018 standard is another extension to 27001, which focuses on privacy controls for public cloud processors hosting customer environments. We cover this in more detail in our recent ISO 27701 webinar.
Why Should We Seek ISO 27701 Certification?
There are several substantial benefits of obtaining 27701 certification, including:
- Builds trust. Achieving 27701 certification demonstrates to your customers, clients, and partners that you take privacy seriously and helps them trust that you will protect their sensitive information. You can use your 27701 certification status as a key ingredient in your advertising, marketing materials, website content, and client communications to reinforce your commitment to data privacy.
- Circumvents Privacy Audits. In some cases having an ISO 27701 certificate will circumvent the need for an independent privacy audit. For example, Microsoft requires most suppliers to undergo an independent privacy audit, but if you are ISO 27701-certified, they may waive this requirement.
- Improves Public Perception. As privacy concerns have significantly escalated in recent years, having an ISO 27701 certificate can go a long way toward improving the public’s perception regarding the privacy practices of your organization.
- Provides Compliance Mapping. Having an ISO 27701-compliant PIMS will help your organization comply with most international data privacy regulations. Achieving 27701 compliance establishes a framework that covers most legal privacy requirements. With that said, you should expect some incremental work to comply with certain caveats and nuances of specific privacy regulations in different geographic regions (e.g., California Privacy Rights Act (CPRA), Virginia Consumer Data Protection Act (VCDPA), and Europe’s General Data Protection Regulation (GDPR). We provide specific examples of how ISO 27701 requirements map to specific privacy regulations in our recent ISO 27701 webinar.
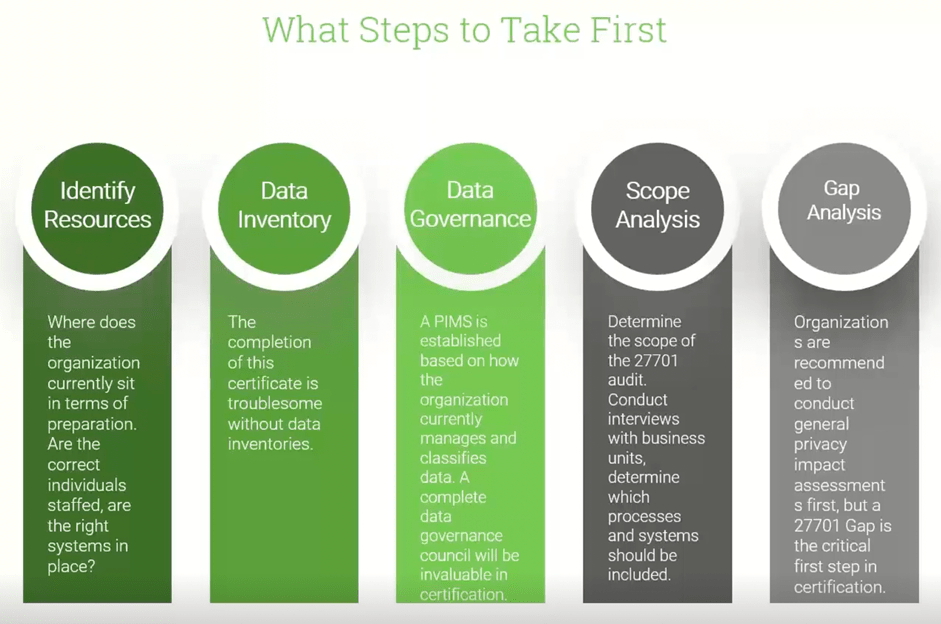
What Steps Should We Take First To Get Certified?
Many of our clients find it challenging to figure out how to begin their journey toward ISO 27701 certification. In the diagram below, we summarize five key steps to getting started. Once you complete these steps, you’ll be well on your way!
Webinar
For a deeper dive on this topic, check out our ISO 27701: Privacy Information Management— Why to Certify webinar.
Additional Resources
Here are some additional Tevora resources on related topics.
- 4 Keys to a Successful ISO 27001 Certification
- Tevora Data Privacy Law Comparison: CCPA, CPRA, GDPR, and PIPEDA
- GDPR is Coming—Are You Prepared?
- CPRA: What Privacy Officers Need to Know
- What to Look for in a DSAR Program?
We Can Help
If you have questions about ISO 27701 or would like help becoming certified for this important privacy standard, just give us a call at (833) 292-1609 or email us at sales@tevora.com.




