May 18, 2021
Using Attack Simulation for Your Incident Response Game
Many businesses struggle to cost-effectively prepare their environment to defend against cyberattacks and respond to incidents in a way that keeps impacts to a minimum. And trying to anticipate and guard against the latest tactics and techniques used by adversaries presents a formidable challenge for even the most skilled security teams.
In this blog post, we’ll describe frameworks and methodologies that can help you defend against, detect, and proactively respond to a broad spectrum of potential cyberattacks. We’ll also discuss ways you can use automated attack simulation tools as a complement to other techniques such as penetration testing, red teaming, and blue teaming to up your Incident Response (IR) game without breaking the bank.
The Incident Response Life Cycle
The most widely adopted methodology for responding to cyberattacks is the Incident Response Life Cycle, which can be summarized as follows:
- Preparation—Prepare environment to defend against cyberattacks. When an incident occurs, gather all relevant documentation relating to compromise from logs and agents throughout the network.
- Identification—Identify Indicators of Compromise (IOC) and Indicators of Attack (IoA) through analysis. Develop a breakdown of events.
- Containment—Contain affected hosts. Gather samples of IoCs for further analysis.
- Eradication—Remove all identified threats from the environment.
- Recovery—Put affected networks and hosts into the recovery phase. Conduct network status checks.
- Lessons Learned—Document all information related to the incident and how it was resolved for future use.
Tevora uses this methodology to help clients respond to incidents, and we have found it to be very effective for remediating incidents quickly and efficiently.
Avoid the “Whack-A-Mole” Trap
We’ve found that it’s important for clients to resist the temptation to rush through the six phases too quickly, which can result in missing some areas that have been affected by the attack. When this happens, clients can end up in a game of “Whack-A-Mole”, with multiple time-consuming iterations required to eradicate all of the threats.
It’s especially important to allow the Identification and Containment phases to fully mature to ensure all threats are addressed. Your ultimate response will likely be faster if you take the needed time to thoroughly complete these critical phases.
Don’t Skip the Lessons Learned
In their hurry to return to normal operations, some clients want to skip the Lessons Learned phase. We strongly recommend completing this phase, which is an extremely effective and valuable way to identify opportunities to shore up your defenses against future attacks.
The Importance of Preparation
Of the six Incident Response Life Cycle stages, Preparation is probably the most important and the hardest to accomplish. That’s where we’re going to focus in this blog post. We’ll cover effective ways to prepare your environment to defend against cyberattacks, including ways to increase your security posture to be ready for adversaries leveraging the latest tools and techniques to attack your network.
Cyber Kill Chain® Framework
One of the best ways to prepare for cyberattacks is to understand the process used by attackers to compromise a victim’s network. The Cyber Kill Chain® framework, developed by Lockheed Martin in 2013, identifies seven steps an adversary must complete to execute a successful cyberattack. This framework can be a great tool for improving your ability to detect and predict intrusions.
The seven steps of the Cyber Kill Chain® are summarized in the following diagram.
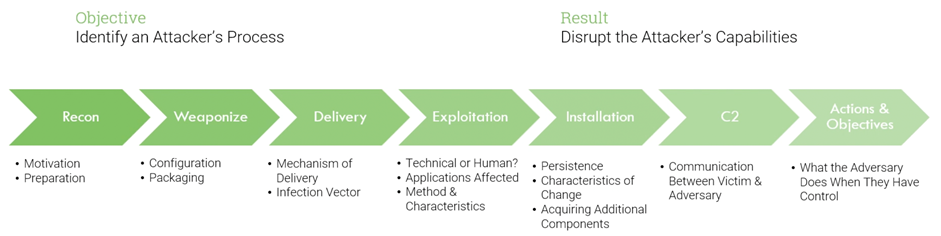
This widely adopted framework has resulted in significant improvements to the traditional detection and incident handling strategies that were in use at the time of its introduction. These traditional strategies focused mainly on post-incident or post-infection detections and how to respond to them.
Cyber Kill Chain®, with its focus on threat intelligence, has driven security teams to develop new, more proactive IR strategies that address emerging tactics and techniques used by adversaries. The framework has guided businesses to develop improved, actionable security intelligence and more effective mitigations and defenses based on the latest adversary tactics and techniques.
Since its introduction, Cyber Kill Chain® has been the go-to model for cyber threat intelligence. It has also served as the precursor and foundation for the MITRE ATT&CK® Framework, which dives even deeper into adversary tactics and techniques.
MITRE ATT&CK® Framework
The MITRE organization was founded during WWII to help the U.S. Department of Defense develop radar and other technologies and has evolved over time to become a cybersecurity industry thought leader.
The MITRE ATT&CK® framework, first published in 2015, is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. It is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
The framework is structured in a matrix format, with 12 columns for general “Tactics,” which represent an adversary’s technical goals for an attack (e.g., Initial Access, Privilege Escalation, Exfiltration).
Rows of the matrix describe “Techniques,” which are specific techniques used by adversaries to accomplish each general Tactic goal (e.g., Drive-by Compromise, Spearphishing, Supply Chain Compromise).
The matrix also provides real-world examples of how techniques have been implemented by specific threat actors. This information can be very helpful in identifying groups that are likely responsible for an attack. For example, in the recent—highly publicized—Solar Winds hack, investigators were able to compare forensic information on the tactics and techniques used by the attackers to the information on threat actor techniques in the MITRE ATT&CK® framework to determine that the APT29 group was likely behind the attack.
The diagram below illustrates the matrix and highlights some of the real-world examples provided for the Spearphishing tactic.
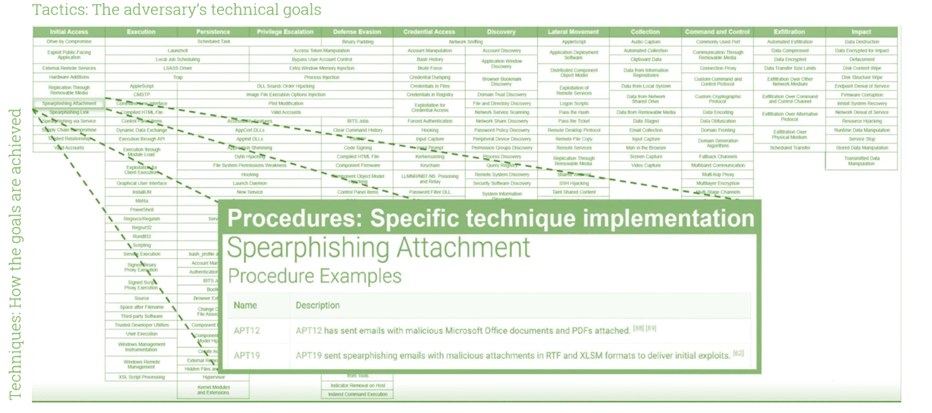
The MITRE ATT&CK® framework, with its real-world information on adversary tactics and techniques, is an excellent resource to help you build a comprehensive and effective IR strategy. Here are some of the key benefits it provides:
- Comprehensive framework of adversary tactics and techniques helps companies develop IR strategies that anticipate a broad range of potential threats. Reduces risk that specific threats will slip between the cracks.
- Can be used to develop mitigating or compensating controls that map to each applicable tactic and technique.
- Real-world information on threat-actor techniques is helpful in identifying the likely group behind an attack.
- The MITRE ATT&CK® Navigator is an easy-to-use online tool that enables you to visualize your defensive coverage across all elements of the matrix. With this tool, you can keep track of information for each tactic/technique combination, including:
- Guides organizations in identifying which tools are addressing which tactics/techniques and areas where tools have overlapping coverage.
Adding Automated Attack Simulation Tools to the Mix
Used in combination, the Cyber Kill Chain® and MITRE ATT&CK® frameworks give you a comprehensive view of the adversary tactics and techniques you need to guard against. With this understanding, you can develop a robust IR strategy that uses multiple techniques to ensure your defenses are prepared for all threats. Traditionally, companies have used pentesting, red teaming, and blue teaming techniques to accomplish this. More recently, security teams have begun employing automated attack simulation tools to complement the traditional techniques.
While automated attack simulation tools alone cannot address all needs, they can be effective for checking defenses against specific types of threats, and they offer many benefits, including:
- Excellent open-source tools are available for free, which can help in reducing security costs.
- Automated scripts can be easily edited to tailor tests to specific environments.
- Tests can be re-run quickly to confirm that deployed defenses are working as expected or test and compare the capabilities of defensive tools.
- A broad range of scripts can be run in rapid succession to cover many attack scenarios in a short period of time.
- Test results are automatically logged for review once execution is complete.
In some cases, automated tests can be used to replicate methods used by pentesters. However, this does not work for all scenarios. For example, in a case where a text file containing credentials is vulnerable to attack, human pentesters are generally better equipped to understand the contents of the file and exploit the credentials to gain access to networks or applications.
Conversely, pentesters are often focused on finding a single entry point to a network, which allows them access to multiple internal systems. They may not find all points of vulnerability in a network. In this case, automated attack simulation tools can offer a nice complement to pentesting by quickly probing many network entry points for vulnerabilities.
An effective incident response strategy will identify and deploy a combination of pentesting, red teaming, blue teaming, and automated attack simulation techniques to cover all potential threat scenarios.
Atomic Red Team
While there are commercially-available tools for simulating attacks (e.g., Breach and Attack Simulation), we have had great success using Red Canary’s open-source Atomic Red Team tool. This tool offers a broad range of highly-portable, easily-editable detection test scripts that map to the MITRE ATT&CK® framework. And it’s free! What’s not too like about that?
To complement the Red Team tool, Tevora has developed a GUI-based execution engine (also free and available on Github) to facilitate automatic execution of multiple scripts in a Windows environment.
Used in combination, these tools offer a highly actionable way to immediately start testing your defense capabilities against a wide variety of attacks.
Tevora’s Attack Simulation Webinar
For a deeper dive on these topics and an Atomic Red Team demo, check out the recording of Tevora’s Leveraging Attack Simulation to Improve Incident Response webinar.
Additional Resources
Here are additional resources that can help you gain a deeper understanding of the topics covered in this blog post.
- Cyber Kill Chain® Framework
- MITRE ATT&CK® Framework
- Red Canary’s Atomic Red Team Tool
- Tevora’s Atomic Red Team Windows Execution Engine Threat Blog Post
- Tevora Attack Simulation Services
We Can Help
If you have attack simulation questions or would like help implementing these powerful tools as part of a comprehensive incident response strategy, Tevora’s team of security specialists can help. Just give us a call at (833) 292-1609 or email us at sales@tevora.com.
About the Author
Matt Mosley is the Director of Incident Response at Tevora.