August 6, 2021
In the Market for EDR Tools? Check Out Our 5 Criteria for Finding the Best Tools for Your Environment.
The continuing growth and sophistication of endpoint attacks and the recent surge in remote work have made it increasingly clear that organizations need robust Endpoint Detection and Response (EDR) solutions. But with the flood of EDR tools on the market, choosing the right tools for your company can be overwhelming!
Fortunately, Tevora has a long and successful track record helping clients select and implement EDR tools, and we’re happy to share what we’ve learned. In this blog post, we’ll provide insights and selection criteria that we’ve used to help our clients find EDR tools that are well-matched to their specific needs.
What is EDR?
Research and advisory firm Gartner describes the EDR market as “solutions that record and store endpoint-system-level behaviors, use various data analytics techniques to detect suspicious system behavior, provide contextual information, block malicious activity, and provide remediation suggestions to restore affected systems. EDR solutions must provide the following four primary capabilities:
- Detect security incidents
- Contain the incident at the endpoint
- Investigate security incidents
- Provide remediation guidance”
You may also encounter instances where these solutions are referred to as Endpoint Threat Detection and Response (ETDR) tools. From our perspective, the names can be used interchangeably.
What Criteria Should We Use to Select EDR Tools?
Based on our experience working with clients, we’ve developed five criteria that have proven to be highly effective for choosing EDR tools.
1. Next-Gen Anomaly Detection (AD)
As endpoint attacks get more sophisticated and the number and variety of endpoint devices grow exponentially, EDR tools must become increasingly intelligent to detect anomalies in endpoint activity that indicate potential cyberattacks. It’s important to find EDR tools that leverage Next-Gen technologies such as machine learning, artificial intelligence, and behavioral analysis to sift through mountains of endpoint-related data in real-time to quickly detect potential threats. The sooner a threat is detected, the sooner it can be contained, which is critical for minimizing damages.
Some tools have the ability to map suspicious behavior to the MITRE ATT&CK Framework, which can help accelerate identification of the type of attack being observed.
2. Threat Feeds and Attack Vectors
Look for EDR tools that incorporate information from leading threat intelligence feeds to understand what threat behaviors and attack vectors to be on the lookout for. Make sure the threat feed information is obtained frequently, if not in real-time, to increase your chances of detecting the latest types of attacks.
The more threat feeds an EDR tool subscribes to, the better; this minimizes the risk that you will miss an emerging attack vector. Accepting feeds from multiple types of threat feed providers (e.g., cybersecurity providers, pure-play feed providers, cybersecurity organizations, and law enforcement entities) can be helpful in identifying a broad range of attack vectors.
3. Response Capabilities
The best EDR tools not only identify and alert staff about potential threats but automatically respond by blocking malicious activity on compromised endpoints and initiating other actions to minimize damages.
Look for tools that have robust live response capabilities that automatically drop into a compromised system to remediate problems or run scripts and commands to help triage the situation. It’s extremely important to find tools that offer these capabilities—and you won’t find them in all EDR solutions—so be sure to make it a priority in your selection process.
If you can’t find an EDR tool with live response capabilities that meets your needs or budget, look for a tool that will at least recommend remediation steps for you, which can help accelerate your response to incidents.
4. Isolation and Containment
Some of the more powerful EDR tools have the ability to isolate and contain potentially compromised endpoints from the rest of your network to prevent malware or intruders from gaining access to your valuable company resources. Containment and isolation can substantially limit or eliminate damage to your environment.
5. Visibility and Compatibility
Make sure the tools you select have visibility to—and are able to perform detection functions on—most or all of your network endpoint devices. Consider that endpoint devices will likely be required to run EDR tool agents. To do this, the agents must be able to run on each of the operating systems used by your endpoint devices (e.g., Windows, Unix, Linux, Mac OS, phone or tablet operating systems, or custom operating systems used for specialized Internet of Things devices such as sensors and cameras).
Where Can We Find Information Comparing EDR Tools?
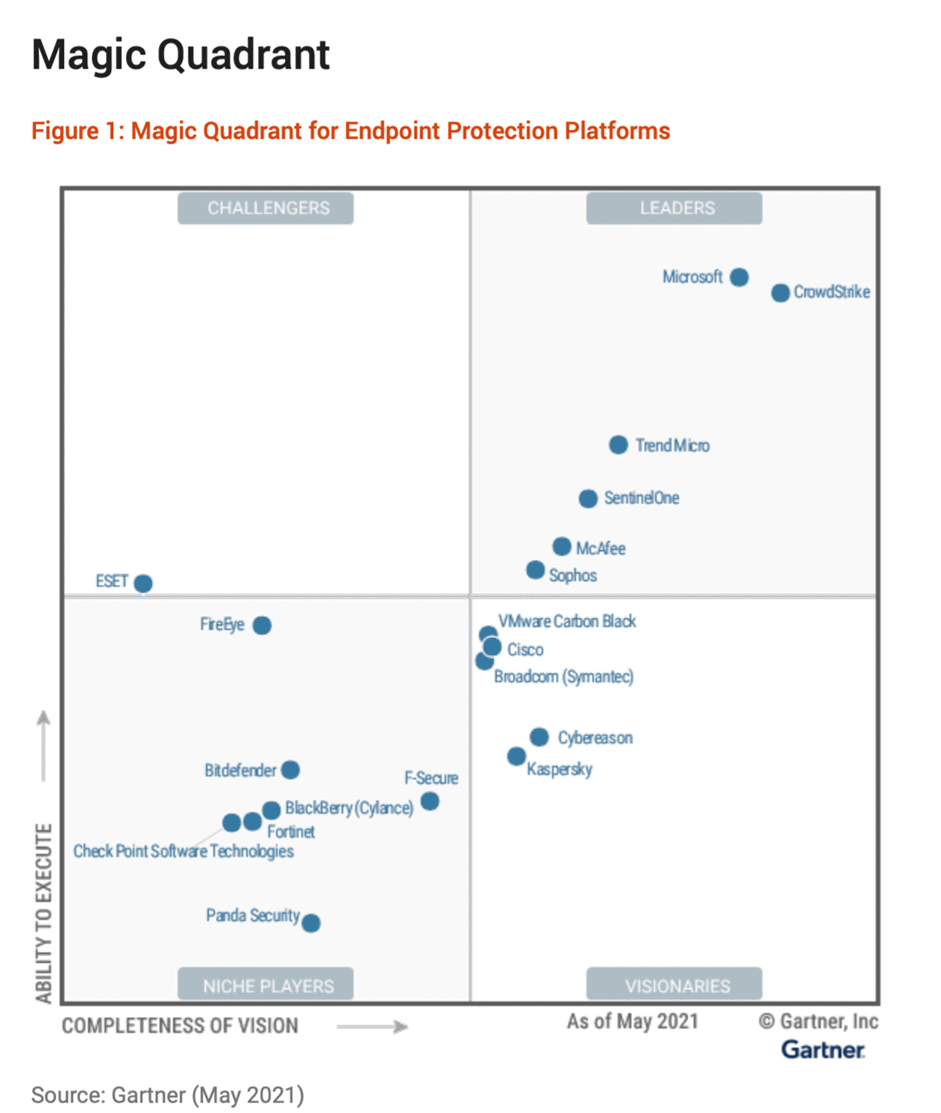
The Gartner Magic Quadrant for Endpoint Protection Platforms report published on May 5, 2021, provides a good comparison of EDR offerings from different vendors, including their respective strengths and weaknesses.
Here’s a chart from the report that summarizes the different vendor offerings based on overall Completeness of Vision and Ability to Execute:
Additional Resources
Check out these additional resources for a deeper dive into EDR in general and specific EDR offerings.
· Red Canary 2021 EDR Buyer’s Guide
· Gartner Endpoint Detection and Response (EDR) Solutions Reviews
· Forrester WaveTM: Enterprise Detection And Response, Q1 2020
We Can Help
If you have questions about EDR tools, need staff training, or would like help selecting tools or testing and implementing them in your environment, Tevora’s team of security specialists can help.
We’ve worked with some of the world’s leading companies to help them with EDR tools and would welcome the chance to guide you in implementing these vitally important solutions. We have experience with a broad range of EDR solutions running on Windows, Unix, Linux, Mac OS, and many other device-specific operating systems. Because we are a consulting firm and not a tools provider, we can be completely objective in helping you select the tools that are right for your organization, regardless of the vendor.
If you would like to learn more about how we can help you with EDR tools, just give us a call at (833) 292-1609 or email us at sales@tevora.com.
About the Author
Matt Mosley is the Director of Incident Response at Tevora.