Apr 18, 2022
PCI DSS Launches Version 4.0
The Payment Card Industry Data Security Standard (PCI DSS) is the leading standard for securing cardholder data and is widely adopted across the payments industry.
PCI DSS version 4.0—published on March 31, 2022—represents a significant upgrade to the previous version (3.2.1). The new version addresses emerging threats to payment data and evolving security and payment technologies.
In this blog post, we’ll review the implementation timeline for PCI DSS 4.0, describe some of the key differences between versions 4.0 and 3.2.1, and provide guidance for preparing your organization to comply with this new version of the standard.
What’s The Timeline for PCI DSS 4.0 Implementation?*
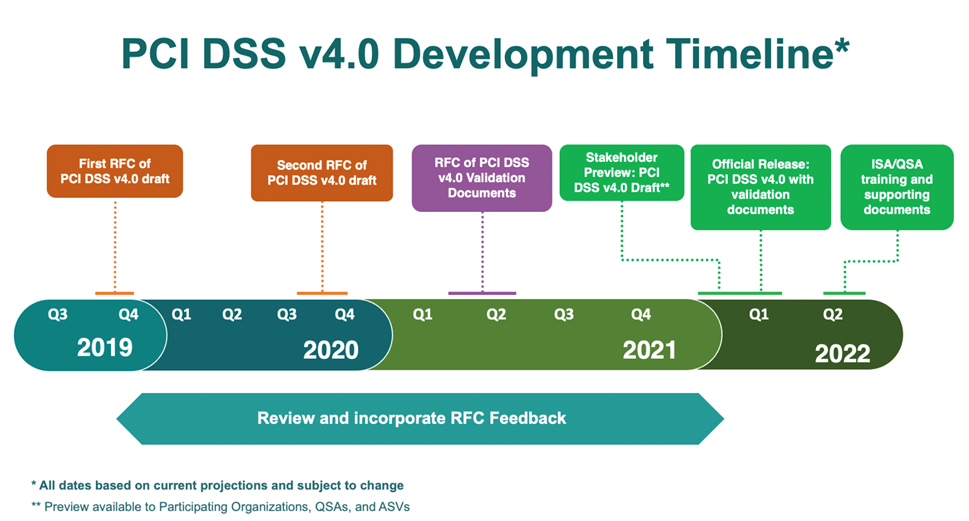
Development Timeline
Leading up to the March 2022 publication of the PCI DSS 4.0 specification, the PCI Security Standards Council published multiple draft versions, incorporating feedback gathered via a Request For Comment (RFC) process with each new draft. Here’s a summary of the development timeline:
Transition Period
The PCI DSS 4.0 implementation plan includes a transition period to allow organizations to bring their environments into compliance with version 4.0. Version 3.2.1 will remain active for 18 months following the publication of all PCI DSS 4.0 materials, including the standard, supporting documents (e.g., SAQs, ROCs, and AOCs), training materials, and program updates. This transition period gives organizations time to update their reporting templates and forms and implement technology, process, and control changes needed to support version 4.0.
PCI DSS version 3.2.1 will be retired at the end of the transition period (currently planned for Q1 2024), leaving version 4.0 as the only active version of the standard.
Future-Dated Requirements
The PCI Security Standards Council (PCI SSC) anticipates there will be a number of new PCI DSS 4.0 requirements published during the transition period based on learnings as the new standard is rolled out. The effective date for these new requirements will be future dated to a date that is expected to be well beyond the planned transition period, with a possible future date being between 2 ½ and 3 years after version 4.0 is published.
Future-dated PCI DSS 4.0 requirements will be considered best practices until the future date is reached. While validation is not required, organizations that have implemented controls to meet the new requirements and are ready to have the controls assessed before the stated future date are encouraged to do so. Once the designated future date is reached, all future-dated requirements will become effective and applicable.
Transition Timeline
Here’s an overview of the currently-planned timeline for the transition to PCI DSS version 4.0:
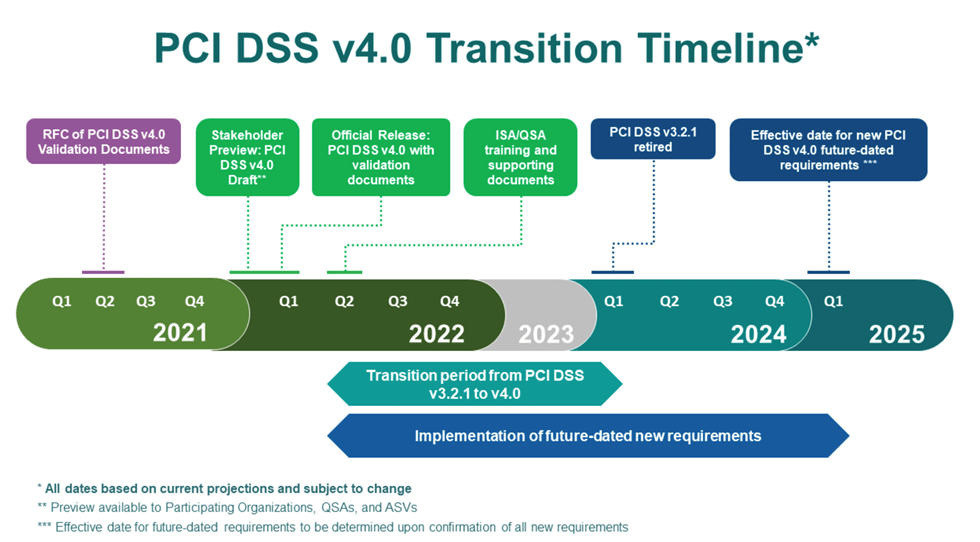
While we don’t yet have specific dates for all of these milestones, we do know that:
- PCI SSC plans to release QSA training for PCI DSS version 4.0 “a couple of months” after the version 4.0 release. QSAs will be able to conduct PCI DSS 4.0 assessments after completing this training.
- PCI DSS version 3.2.1 will be retired on March 31, 2024.
- The new PCI DSS version 4.0 requirements will be fully effective on March 31, 2025.
PCI DSS Version 4.0 Preview
PCI DSS version 4.0 includes a substantial number of changes. Some are paradigm shifts or significant new or modified requirements. Others are smaller refinements or clarifications to requirements. This section provides a preview of the most significant changes.
Paradigm Shift for “Approaching” PCI DSS
Under PCI DSS version 3.2.1, organizations must implement and validate PCI DSS requirements using the “Defined Approach.” This traditional approach uses prescribed “Requirements” and “Testing Procedures” and permits implementation of “Compensating Controls.”
PCI DSS 4.0 allows organizations to use a new “Customized Approach” for implementing and validating requirements. This approach considers the intent of each PCI DSS security objective and allows entities to design their own security controls to meet it. After determining the security control for a given security objective, an organization must provide full documentation to enable their Qualified Security Auditor (QSA) to review it for completeness and alignment to the defined objective. This provides flexibility for companies to use a broader range of methods and technologies to achieve each PCI DSS objective.
The Customized Approach is intended for mature organizations that are capable of developing extensive processes and documentation to support the approach, including “Targeted Risk Analysis” for each customized control.
Organizations that don’t want to use the Customized Approach still have the option to use the Defined Approach.
Targeted Risk Analysis
PCI DSS 4.0 introduces the concept of a “Targeted Risk Analysis,” which applies not only to “Customized” controls but also many other controls related to “frequency.” The following are examples of requirements for which Target Risk Analysis applies under version 4.0:
- 5.2.3.1 – The frequency of periodic evaluations of system components identified as not at risk for malware is defined in the entity’s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1.
- 10.4.2.1 – The frequency of periodic log reviews for all other system components (not defined in Requirement 10.4.1) is defined in the entity’s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1.
- 9.5.1.2.1 – The frequency of periodic POI device inspections and the type of inspections performed is defined in the entity’s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1.
New PCI DSS Version 4.0 Requirements
PCI DSS version 4.0 includes three types of changes:
- Evolving Requirement—Changes to ensure that the standard is up to date with emerging threats and technologies and changes in the payment industry. Examples included new or modified requirements or testing procedures or the removal of a requirement.
- Clarification or Guidance—Updated wording, explanation, definition, additional guidance, and/or instruction to increase understanding or provide further information or guidance on a particular topic.
- Structure or Format—Reorganization of content, including combining, separating, and renumbering of requirements to align content.
Here are some examples of Evolving Requirements included in version 4.0:
- Requirements for securing web applications:
- 6.4.3 All payment page scripts that are loaded and executed in the consumer’s browser are managed as follows:
- A method is implemented to confirm that each script is authorized.
- A method is implemented to assure the integrity of each script.
- An inventory of all scripts is maintained with written justification as to why each is necessary.
- 11.6.1 A change- and tamper-detection mechanism is deployed as follows:
- To alert personnel to unauthorized modification (including indicators of compromise, changes, additions, and deletions) to the HTTP headers and the contents of payment pages as received by the consumer browser.
- The mechanism is configured to evaluate the received HTTP header and payment page.
- 6.4.3 All payment page scripts that are loaded and executed in the consumer’s browser are managed as follows:
There is a new emphasis on measures to preventing digital skimmers. Organizations will need to implement additional web application security measures, such as enforcing a Content Security Policy, to control rogue scripts that may load on your payment pages.
- Requirements for Work from Home (WFH) users handling cardholder data:
- 3.4.2 When using remote-access technologies, technical controls prevent copy and/or relocation of PAN for all personnel, except for those with documented, explicit authorization and a legitimate, defined business need.
Organizations now have additional considerations for protecting cardholder data on remote workstations as PCI SSC increases emphasis on data leak/loss prevention controls. There are different options for fulfilling this requirement, which may include the use of data loss prevention solutions, limiting ability to use copy and paste functions on virtual terminals, and implementing restrictions on removable storage media.
- Requirements to update security awareness training program to include a greater emphasis on social engineering and phishing:
- 5.4.1 Processes and automated mechanisms are in place to detect and protect personnel against phishing attacks.
- 12.6.3.1 Security awareness training includes awareness of threats and vulnerabilities that could impact the security of the CDE, including but not limited to:
- Phishing and related attacks.
- Social engineering.
A good example of a requirement that has been reworded is Requirement 1 regarding network security. Here are the specific wording changes:
- Version 3.2.1: “Requirement 1: Install and maintain a firewall configuration to protect cardholder data”
- Version 4.0: “Requirement 1: Install and maintain network security controls to adapt to modern virtualized environment”
In addition, terms such as “Firewalls,” “Routers,” and “DMZ,” that are not applicable to cloud-based deployments have been removed from the version 4.0 requirements.
While we’ve touched on some of the most significant changes, there are many other requirements changes in areas such as acceptable hashing algorithms, appropriate use of disk encryption, network-level malware detection, and additional documentation requirements.
How Can We Prepare for PCI DSS Compliance?
Tevora has been a certified PCI QSA since the PCI DSS standard was created in 2004. With almost two decades serving as a trusted security assessor for some of the top companies in North America, Tevora’s proven, efficient, and cost-effective methodology can help guide your PCI DSS compliance efforts.
Our team of PCI DSS specialists has an in-depth understanding of the version 4.0 requirements and can leverage this expertise to help you efficiently navigate the new requirements.
We’re happy to help you comply with PCI DSS version 3.2.1 or work with you to proactively comply with version 4.0. Our simple compliance process can be summarized as follows:
- Gap Analysis. Tevora works with your team to outline strategies for a cost-effective road to PCI DSS compliance. In addition to scope reduction, our QSAs assess and validate security controls early in the process so remediation efforts can be directed and focused.
- Remediation. Whether it is writing security policies or implementing security controls, working with our QSAs offers expertise to accurately diagnose liabilities and select effective methods for attaining compliance.
- Certification. As your trusted advisor, Tevora ensures your PCI DSS compliance initiatives are executed in confidence and on time.
- Health Checks. Tevora’s Health Checks are mid-year checkups that help you stay current with compliance requirements in between annual certifications. They generally focus on changes to the environment, high-risk areas, and security controls that require manual processes.
Additional Resources
Here are some additional Tevora resources that provide a deeper dive on the PCI DSS version 4.0 implementation:
- Requirements and Security Assessment Procedures v4.0
- Summary of Changes from PCI DSS v3.2.1 to PCI DSS v4.0
- Tevora PCI DSS Compliance Datasheet.
We Can Help
If you have questions about PCI DSS version 4.0 or would like help becoming certified for this substantial PCI DSS update, just give us a call at (833) 292-1609 or email us at sales@tevora.com.
*[1] Based on information from the PCI Security Standards Council’s Updated PCI DSS v4.0 Timeline blog.