Aug 15, 2023
Revolutionizing Cybersecurity: Unveiling FedRAMP Revision 5
On May 30, 2023, three years after the release of NIST Special Publication 800-53 Revision 5 Security and Privacy Controls for Information Systems and Organizations, the FedRAMP Joint Authorization Board (JAB) finally approved and released the FedRAMP Revision 5 baselines. To help cloud service providers (CSPs) who work with or wish to work with federal agencies move toward this change, the FedRAMP Program Management Office (PMO) has released the FedRAMP Baseline Revision 5 Transition Plan.
This blog post will review significant changes to the FedRAMP controls from Revision 4, provide an overview of the Transition Plan, recommendations for CSPs during the transition, and how Tevora can help this seemingly ambitious endeavor.
What is FedRAMP?
The Federal Risk and Authorization Management Program (FedRAMP) is a US government program that reviews CSPs and authorizes those CSPs with sufficient security controls in place to work with US federal agencies to maintain compliance with the Federal Information Security Modernization Act (FISMA), which requires agencies to protect federal information. The program helps maximize efficiency by federal agencies, promotes the adoption of cloud technology or services by federal agencies, and provides reasonable assurance that the CSP will sufficiently protect the federal information it will be processed on behalf of the federal contracting agency.
The Office of Management and Budget (OMB) Circular A-130 requires federal agencies implementing FISMA to use NIST standards and guidance. As such, FedRAMP’s controls are based on NIST 800-53 controls, with minor tailoring’s such as FedRAMP-specific parameters and differing required controls per baseline. Like NIST 800-53, FedRAMP has three standards baselines an organization may strive to adhere to—Low, Moderate, and High. There is also Low Impact-Software as a Service (LI-SaaS), but there are some conditions the CSP must meet to qualify for the LI-SaaS baseline.
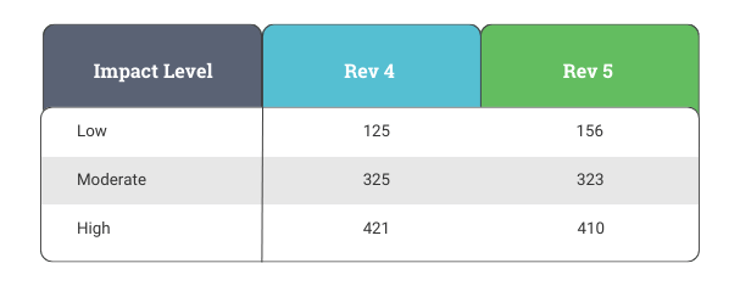
Each baseline has a different number of required controls. Not only has the number of controls needed changed with the transition to Revision 5, including some net new controls, but the changes to specific controls’ language have also impacted the meaning.
Meeting these controls is not the only requirement for FedRAMP authorization. Becoming FedRAMP authorized heavily relies on accurate documentation of the security controls, the CSPs environment or infrastructure, data in scope, penetration testing, plan of action and milestones (POAM), and more. Most importantly, CSPs are expected to maintain this documentation and continuously monitor their environment to stay authorized.
Changes
Higher-Level Changes
New Revision 5 Templates
FedRAMP authorization relies heavily on accurate documentation, which requires using official templates that were released on June 30, 2023. These templates can be found at FedRAMP’s official Documents & Templates page here.
With the new Revision 5 templates, CSPs and assessors should look forward to a more streamlined, consolidated System Security Plan (SSP). The same template will be used for all baselines instead of requiring CSPs to attach baseline-specific appendices to the SSP.
Updated OSCAL Content
FedRAMP Open Security Controls Assessment Language (OSCAL) files are now available here to reflect Revision 5 baselines. The use of OSCAL is not mandatory for FedRAMP authorization but is immensely useful for the efficiency of the authorization process and for easy maintenance of the required documents. Because technology constantly changes, CSPs should use these files to find ways to standardize and automate documentation for increased flexibility and decreased manual effort after any control changes. It is not unreasonable to expect OSCAL documents or similar language for automating document updates to be required in a future revision of FedRAMP.
Supply-Chain Risk (SR) Family Added
The SR family of controls has been added to reflect NIST 800-53 Revision 5 changes. Supply-chain risks were initially addressed within the System and Services Acquisition (SA) family, mainly through SA-12 (Supply Chain Protection). However, that specific control was only required for CSPs aiming for a high baseline. Having a mature third-party risk management or supply chain risk management program in place becomes crucial due to the emphasis on controls and requirements associated with the extensive range of baselines within the new SR family.
Security AND Privacy
Much of the language within the controls’ descriptions and discussions have been updated to include privacy, reflecting the dependency and importance between both security and privacy controls. For example, CM-4 (2) (Configuration Management | Impact Analyses | Verification of Controls) has been updated to state, “After system changes, verify that the impacted controls are implemented correctly, operating as intended, and producing the desired outcome with regard to meeting the security and privacy requirements for the system.”
While many assume that a secure system inherently means privacy is protected, there may be instances where the functionality of a system or service runs as needed but violates privacy requirements. Consider a scenario where an application performs regular backups of data that an end user has input into the application and then maintains that backup for a year—although considered a best practice in terms of security, there may be privacy implications if, for example, the end user is a minor and has input their data.
Some Control-Specific Changes or Additions
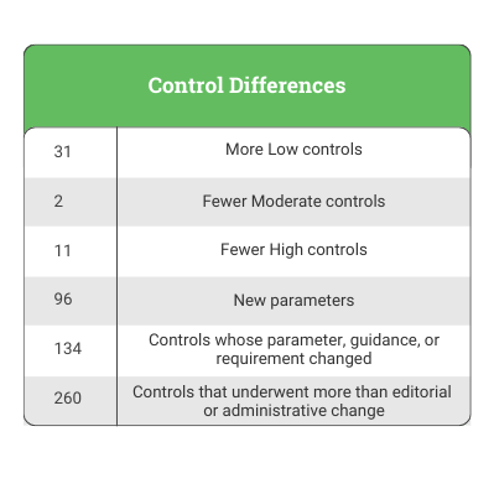
The following table does not reflect all control changes or new controls but instead lists a few controls we thought–at the time of this writing–were interesting enough to highlight, such as new controls or parameters that may require significant process changes.
| Control | Control Title | Tevora’s Thoughts |
| AC-2 and control enhancements | Account Management | The text and parameters have been updated to include stricter timelines for notifying account managers of changes to personnel or account needs. For example, the FedRAMP assignments for notification when personnel have been terminated is now eight hours. Although it is best practice to notify account managers right away, in practice we have seen many companies neglect to notify account managers or have seen many companies that have a notification process in place but do not follow up by disabling or deleting the account. On a related note, many AC-2 control enhancements have been updated to require or recommend automated mechanisms for account management (e.g., automatically disabling accounts upon termination). |
| CA-7 and CA-7 (4) | Continuous Monitoring | This control now requires monthly “Operating System, Database, Web Application, Container, and Service Configuration” scans, in addition to scans performed by an independent assessor at least annually, as part of the CSP’s continuous monitoring program. CA-7 (4) requires risk monitoring to be a key component to the program, including both security and privacy risks. CSPs with an Agency Authorization to Operate (ATO) should reference the Agency Guide for Multi-Agency Continuous Monitoring, while CSPs with a Joint Authorization Board (JAB) Provisional Authorization to Operate (P-ATO) should reference the Continuous Monitoring Strategy Guide when developing their plan or program, although both documents provide helpful information for continuous monitoring programs regardless of authorization. |
| CA-8 (2) | Red Team Exercises | Although CA-8 requires penetration testing, CA-8 (2) takes this a step further by requiring the CSP (or an external firm enlisted by the CSP) to perform red team exercises that simulate more real-world or adversarial scenarios. The specific exercises may be defined by the organization and tailored to the system or mission-critical business functions. As opposed to a penetration test report, these exercises may result in an assessment with a broader scope or may provide an organization with a generalized idea of areas to improve security and privacy controls, rather than specific vulnerabilities or findings. Most notably, although this is now a newly required control in FedRAMP baseline Moderate and High, the FedRAMP PMO representatives stated during the Office Hours session that they do not plan on updating the FedRAMP Penetration Guidance document. |
| IA-12 and control enhancements | Identity Proofing | This set of controls requires proof of identity when registering users or creating accounts and is based on NIST SP 800-63a Digital Identity Guidelines: Enrollment and Identity Proofing. Implementation of the controls should be tailored to the appropriate Identity Assurance Level (IAL)–IAL1, IAL2, and IAL3–described in NIST SP 500-63. |
| PS-9 | Position Descriptions | This new base control requires CSPs in security and privacy roles to be specified in organizational position descriptions. Note that the control does not require individual personnel to fulfill one privacy role or one security role. It simply requires the CSP to document within position descriptions the required security and privacy roles or responsibilities for that position. |
| RA-5 (11) | Public Disclosure Program | This new control enhancement is required for all baselines. CSPs should provide an easily accessible channel for the public to report vulnerabilities discovered in good faith. The language should be clear and should not condition reports on indefinite non-disclosure, but CSPs may request a reasonable timeframe to remediate the reported vulnerability. |
| RA-7 | Risk Response | CSPs are now required to respond to findings from security and privacy assessments, audits, and monitoring. The emphasis of this control is not just to remediate (or accept, transfer, avoid) risk findings but to determine risk tolerance prior to making risk decisions and, more importantly, to generate a plan if the mitigation is not immediate. |
Transitioning from Revision 4 to Revision 5
As stated by FedRAMP, the requirements and timelines for CSPs to be able to transition to the Revision 5 baseline and templates depend on the CSP’s current FedRAMP authorization phase. CSPs need to determine the phase that they are in to determine the corresponding transition timeline.
The various phases are listed as:
- Planning
- Initiation
- Continuous Monitoring
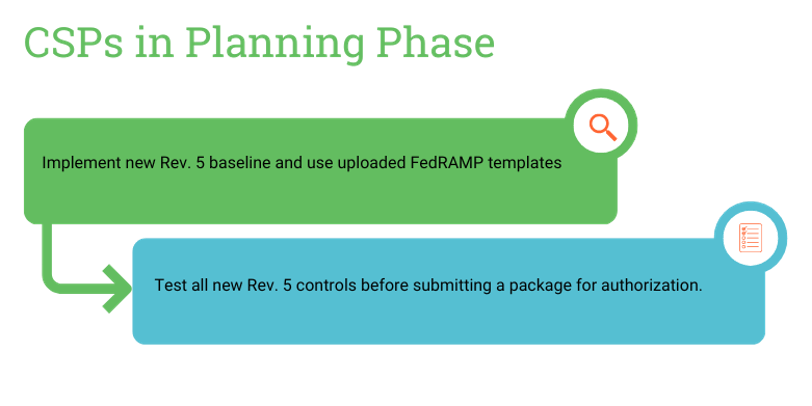
For CSPs in the Planning phase, the assessor will test the Revision 5 baseline prior to submitting a package for authorization if the following applies to the CSP:
- They are in the readiness review process.
- They have not yet partnered with a federal agency (before May 30, 2023)
- They have not yet contracted with a 3PAO for Revision 4 assessment (before May 30, 2023)
- CSPs with JAB prioritization that have not yet begun an assessment after the release of Revision 5
CSPs in the Planning phase should move forward with Rev. 5 baselines, controls, and templates.
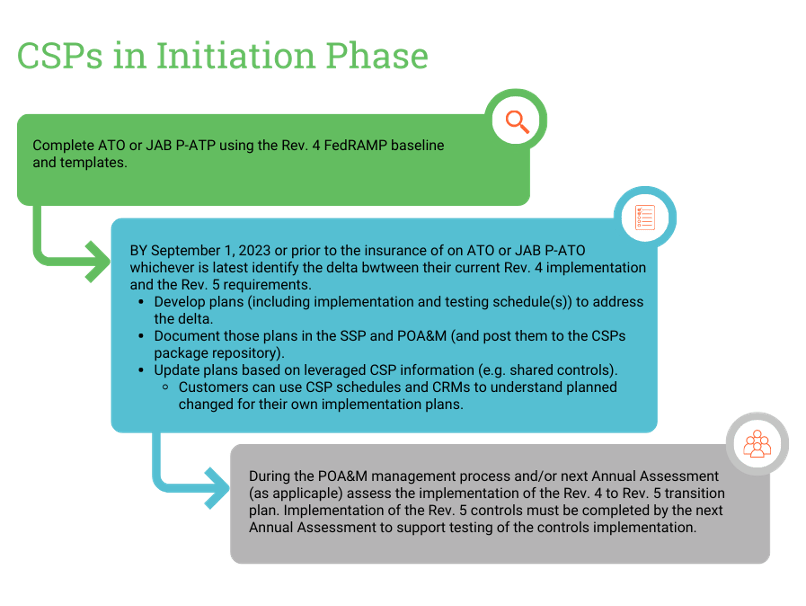
CSPs are in the Initiation phase if the following applies:
- Currently prioritized for the JAB and under contract with a 3PAO/assessment and working towards P-ATO package submission, or have already initiated the JAB P-ATO review process (before May 30, 2023)
- Have partnered with a federal agency, are under contract with a 3PAO, are being assessed by a 3PAO, or have been assessed and submitted the package for Agency ATO (before May 30, 2023)
As shown in the screenshot below, CSPs in the Initiation phase should identify deltas between Rev. 4 implementations of controls and the Rev. 5 requirements. FedRAMP PMO has stated that if the Rev. 4 implementation meets or exceeds the new Rev. 5 requirement, then plans to address those deltas are not required.
Lastly, CSP’s are classified to be in the Continuous Monitoring phase if any of the following applies:
- The CSP is in continuous monitoring with a current FedRAMP Authorization
Suppose their last assessment was performed between January 2, 2023, and July 3, 2023. That that case, then CSPs in the Continuous Monitoring phase have at most one year to implement and test all items documented in their POA&Ms. Continuous Monitoring CSPs who perform their annual assessments between July 3, 2023, and December 15, 2023 must complete all implementation and testing activities before their following yearly assessment.
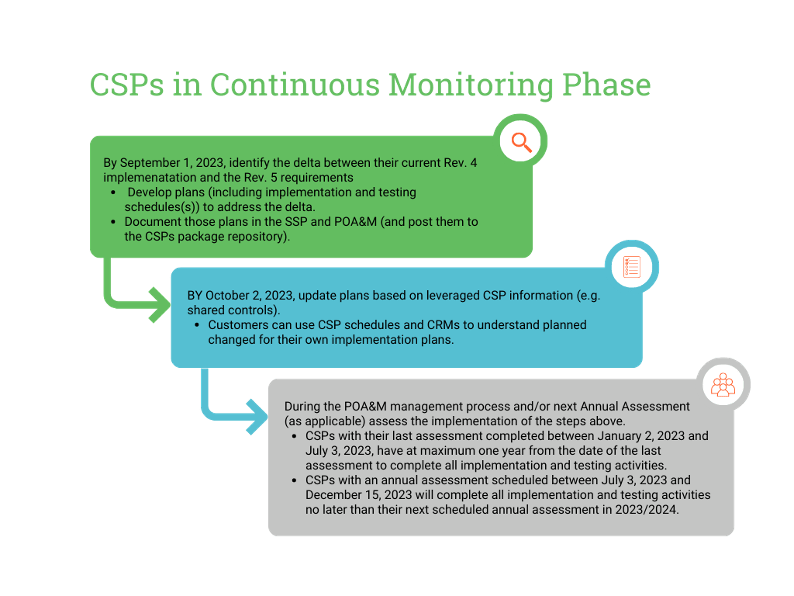
Regardless of what phase the CSP is in, all CSPs (with their Assessors) must perform the following:
- Develop Schedule–Completing of the Rev. 5 System Security Plan (SSP), Security Assessment Plan (SAP), conducting testing, and POA&Ms should be scheduled with clear timeframes.
- Update Documentation to FedRAMP Rev. 5 Templates–CSPS must update their documentation to the FedRAMP Rev. 5 templates. The CSP’s specific phase may impact how exactly certain controls are documented, but regardless CSPs should be working on transitioning their documentation over to Rev. 5 templates. Controls that are not met but will (hopefully) be implemented should be included clearly in the developed schedule.
- Determine Scope of Assessment–This may be more relevant to CSPs in the Initiation or Continuous Monitoring phases than the Planning phase, as this involves identifying the deltas between Rev. 4 controls and Rev. 5 controls to see what must be tested. However, even CSPs in the Planning phase should determine the scope of the assessment as some controlled testing may still need to be performed based on the CSP-specific implementation.
While the transition from Revision 4 to Revision 5 may seem overwhelming, especially considering the timeframe between the release of the required template documents and the deadline for CSPs and 3PAOs to update said documents is relatively short, FedRAMP PMO has made it clear that being open and communicative with the authorizing official (AO) will significantly help with the transition, as AOs have been instructed to work with CSPs and assess any extenuating circumstances or exceptions within reason; for example, if the CSP has signed a contract with a 3PAO but the time of the assessment was pushed back, leaving very little time to complete documentation by September 1, 2023, the AO may consider this limited timeframe.
Having a clear plan with communication to all relevant stakeholders will help demonstrate to the AO that the CSP is working towards these changes and will help CSPs strategically implement the changes.
How Can Tevora Help?
For CSPs who have already gone through part of the FedRAMP process, particularly those in the Initiation or Continuous Monitoring phases, the required timeline to move from Revision 4 to Revision 5 may seem daunting and almost impossible. Smaller or midsized companies without additional resources to spare may feel more pressure. However, Tevora has the expertise and skills to simplify the transition.
As an authorized FedRAMP 3PAO, we have extensive experience assessing CSPs, performing the required penetration tests, and working directly with FedRAMP PMO personnel. Our personnel can help during the Schedule Development to help with the transition. Our team can update your documentation, leaving your resources free to focus on critical business functions. To not only meet but exceed the standards set by the new Supply Chain Risk family, our Third-Party Risk Management services are available to improve, maintain, or even create your company’s vendor risk management programs. Our Federal and Enterprise Risk Management teams can also help update or create IT security policies to adhere to these changes or new controls.
No matter your needs, Tevora has the resources and skills to make the transition as seamless as possible. Please get in touch with us if you have any questions regarding FedRAMP or any other cybersecurity inquiries. Just give us a call at (833) 292-1609 or email us at sales@tevora.com.