Sep 12, 2023
Turbocharge Your Cyber Resilience with Continuous Threat Exposure Management
As organizations evolve their technical and security environments to embrace emerging trends such as multi-cloud infrastructures, dispersed work practices, SaaS solutions, and growing constellations of IoT devices, their attack surfaces are becoming increasingly complex and fragmented. These ever-expanding attack surfaces make it more difficult for CISOs to manage threat exposure effectively.
In recent years, the Continuous Threat Exposure Management (CTEM) process has emerged as a practical approach for helping organizations manage threats and vulnerabilities in today’s complex environments. In this blog post, we’ll describe the CTEM process and demonstrate how it can be adapted for use in your environment.
What is CTEM[1]?
The CTEM process was developed by the research and consulting firm Gartner®, which describes it as a “set of processes and capabilities that allow enterprises to continually and consistently evaluate the accessibility, exposure, and exploitability of an enterprise’s digital and physical assets.”
The five stages of the CTEM cycle are designed to help organizations continually monitor, evaluate, and reduce their level of exploitability and validate that their analysis and remediation processes are optimal. According to a Gartner® report[2], “The objective of CTEM is to get a consistent, actionable security posture remediation and improvement plan that business executives can understand, and architecture teams can act upon.”
The five stages of the CTEM cycle are described below.
Continuous Threat Exposure Management (CTEM) Cycle
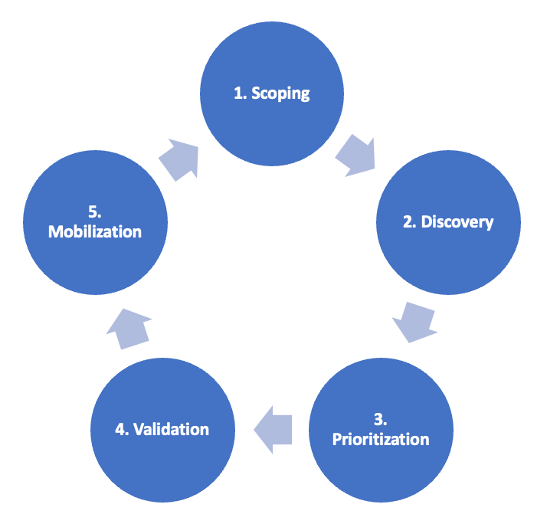
1. Scoping
For most large organizations, their attack surface exceeds the scope of their vulnerability management programs. With CTEM, the scope needs to evolve to encompass an extended set of assets—from traditional devices, apps, and applications to fewer tangible elements (such as corporate social media accounts, online code repositories, and integrated supply chain systems). An effective way to address this is to identify an initial scope, including a plan to prove value to stakeholders and expand this scope over time as the program progresses.
To define and later refine the scope of the CTEM initiative, security teams must first understand what is essential to their business counterparts and what impacts (such as a required interruption of a production system) are likely to be severe enough to warrant the collaborative remedial effort.
More developed vulnerability management projects generally include good initial scoping for internal, on-premises, and owned assets. A CTEM program goes beyond self-inflicted vulnerabilities and takes the “attacker’s view” beyond the traditional common vulnerabilities and exposures (CVEs). When trying to find the right scoping for a CTEM program pilot, good candidates include:
- External attack surface—It combines a relatively narrow scope (for most organizations) and a growing ecosystem of tools.
- SaaS security posture—While tool maturity is still lacking, expanding remote workforces has led to more critical business data being hosted on SaaS, ensuring more accessible communication about risks.
Later cycles could expand to include:
- Digital risk protection, which adds greater visibility into the attack surface.
- Dark and deep web sources to identify potential threats to critical assets and provide contextual information on threat actors and the tactics and processes utilized to conduct malicious activity.
2. Discovery
Once scoping is complete, it is vital to begin discovering assets and their risk profiles. Priority should be given to discovering areas of the business that the scoping process has identified, although this isn’t always the driver.
Exposure discovery goes beyond vulnerabilities. It can include misconfiguration of assets, security controls, and other weaknesses such as counterfeit assets or unsatisfactory responses to a phishing test.
As many discovery processes go beyond the initially-stated scope—to identify visible and hidden assets, vulnerabilities, misconfiguration, and other risks—the focus should next shift to the “prioritization” step, where additional “noise cutting” is necessary.
3. Prioritization
The goal of exposure management is not to try to remediate every issue identified or the most zero-day threats, for example, but rather to identify and address the threats most likely to be exploited against the organization.
Organizations should be open to the traditional ways of prioritizing exposures via predefined base severity scores. They need to account for exploit prevalence, available controls, mitigation options, and business criticality to reflect the potential impact on the organization. More mature organizations should apply the lessons learned from conducting and expanding their vulnerability management program.
Prioritizing the treatment of exposures should be based on a combination of exposure urgency and severity, availability of compensating controls, risk appetite, and level of risk posed to the organization. In other words, organizations should determine their high-value assets (location of critical business value) and focus treatment efforts where appropriate depending on whether existing security controls are in place and the likelihood of as asset’s exploitation by an adversary.
In addition to prioritizing risk remediation, A CTEM program should include the rationale for reductions in risk priority based on the topology/configuration/criticality of the systems under examination.
The program should clearly articulate the organization’s approach to addressing mission-/business-critical systems as a priority. It should also describe the organization’s reaction process for unusual or exceptional events such as zero-days and/or critical vulnerabilities requiring immediate response.
Even an articulated list of prioritized treatments (e.g., patches, signatures, configuration changes) might not be enough to trigger the required collaborative approach to remediating the highlighted issues.
This is why the validation and mobilization steps of CTEM are key to success.
4. Validation
In a security program context, “validation” is part of how an organization can validate how potential attackers can exploit an identified exposure and how monitoring and control systems might react. Validation generally uses controlled simulation or emulation of attackers’ techniques in production environments. While not limited to attackers’ methods, the “validation step” often relies on manual assessment activities, such as red team exercises, to extend its reach. In a CTEM context, it also includes verifying of the suggested treatments, not only for security efficacy but also for organizational feasibility.
The validation step should achieve three objectives:
- Assess the likely “attack success” by confirming that attackers could exploit the previously discovered and prioritized exposures.
- Estimate the “highest potential impact” by pivoting beyond the initial footprint and analyzing all potential attack paths to a critical business asset.
- Determine if the processes to respond to and remediate the identified issues are fast enough and adequate for the business.
A good validation process needs to overcome a few challenges. It requires a mix of technical assessments (e.g., pen testing, red teaming, breach and attack simulation, and attack path analysis) and organizational acceptance. Each organization needs to determine the minimum level of accuracy that will convince all business stakeholders to remediate. This will influence the tool selection and the required procedures.
The validation scope must include the relevant threat vectors and the possibility of pivot and lateral movement. It should also go beyond security controls testing and evaluate the efficacy of procedures and processes.
5. Mobilization
To ensure success, security leaders must acknowledge and communicate to all stakeholders that remediation cannot be fully automated. Many mature organizations have hit the limits of so-called “automated remediation” as technical treatments are often limited to patching, a basic threat detection rule, or a configuration change in security control. A fully automated reaction, recommended by a tool, might be appropriate for the most prominent and hidden issues. This can be an acceptable first step, but it is rarely where security teams struggle.
To rely entirely on the promise of automated remediation in the program will lead to inevitable failure because the consequences of any attempt to remediate fall beyond the sole domain of the security teams:
- There is more than one “fix” (runtime control, patch)
- There is no acceptable “fix” (business interruption)
When a diagnostic tool also suggests a “fix,” it might not necessarily be the best for the organization or be unacceptable for business leaders. There is no way for a tool or a security process to guess what will be acceptable for other teams.
Security tools in a CTEM program suggest only one solution where there may be many. Choosing between these proposed solutions is only predicated on a portion of the available information. The “mobilization” effort aims to ensure the teams operationalize the CTEM findings by reducing friction in approval implementation processes and mitigation deployments. It requires organizations to define communication standards (information requirements) and document cross-team approval workflows. It also requires having business leaders on board and involved.
At higher maturity levels, “mobilization” also requires an evolution of tools to better integrate to deliver context to other parts of the organization, such as the incident response team.
We Can Help
Tevora’s team of cybersecurity experts has extensive experience partnering with clients to design and implement CTEM programs. In addition to helping you develop CTEM requirements customized for your environment, we offer a wide range of services to help you implement your program, including:
- Penetration Testing
- Red Teaming
- Adversary Simulation
- Incident Response Preparation
- Ransomware Preparedness
- Attack Path Analysis
Additional Resources
Below are additional resources that provide a deeper dive into the topics covered in this blog post:
- Attack Simulation Services Datasheet
- Incident Response Readiness Assessment Datasheet
- Compromise Assessment Datasheet
- Internet of Things (IoT) Penetration Testing Datasheet
- Application Penetration Testing Datasheet
- Red Teaming with Physical Penetration Testing and Social Engineering
- Stopping Ransomware by Managing Third-Party Risks
Contact Us
If you have questions about Continuous Threat Exposure Management or would like help implementing a CTEM program in your environment, our team of experienced security experts can help. Give us a call at (833) 292-1609 or email us at sales@tevora.com.
[1] Gartner
[2] Gartner, July 2022, Implement a Continuous Threat Exposure Management (CTEM) Program