March 5, 2024
Exploring the Enhanced NIST Cybersecurity Framework 2.0: Empowering Organizations to Strengthen Cyber Defenses
The National Institute of Standards and Technology (NIST) recently released its newly updated Cybersecurity Framework (NIST CSF) version 2.0. The NIST CSF is a voluntary guidance aimed towards helping organizations better understand, assess, prioritize, and communicate their cybersecurity program efforts. A set of security controls and guidelines designed to help businesses manage and reduce their cybersecurity risks while maintaining a high level of customization to meet a business’s operational mission and strategy.
Highlights:
- The framework documentation and the supplemental guidance are now more detailed and easier to understand. Additionally, NIST CSF 2.0 offers a searchable catalog of information references that allow organizations to cross-reference CSF guidance with other cybersecurity documents (including 800-53 Rev 5 and others).
- The addition of a much anticipated and needed GOVERN function.
- CSF 2.0 supports the implementation of the National Cybersecurity Strategy, therefore expanding its scope to not just protect critical infrastructure, such as hospitals and power plants, but organizations in any industry vertical.
- More clarity around specific use cases via implementation examples for each category and subcategory
- Additional emphasis on Supply Chain Risk Management. Which has been moved to the GOVERN function with added subcategories.
- NIST CSF Version 1.1 had five (5) core functions whereas NIST CSF Version 2.0 has six (6) core functions.
- If you are a small-to-medium sized business (SMB), non-profit, or school-based with cybersecurity program development or enhancements to your risk management strategy on the roadmap for 2024 you can finally kick start your efforts via the Small Business Quick-Start Guide
Key Changes:
The updates to NIST CSF 2.0 are primarily focused on improving an organization’s cybersecurity governance, supplier and third-party risk, and additional recommendations on control implementation. The most striking change within CSF 2.0 is the introduction of the GOVERN function. While the GOVERN function has overlap with the other CSF functions, the newly added GOVERN function highlights the significance of making strategic decisions in cybersecurity via program development, risk management, and supplier risk management.
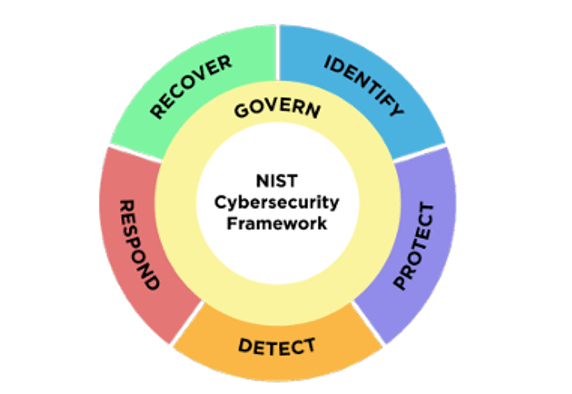
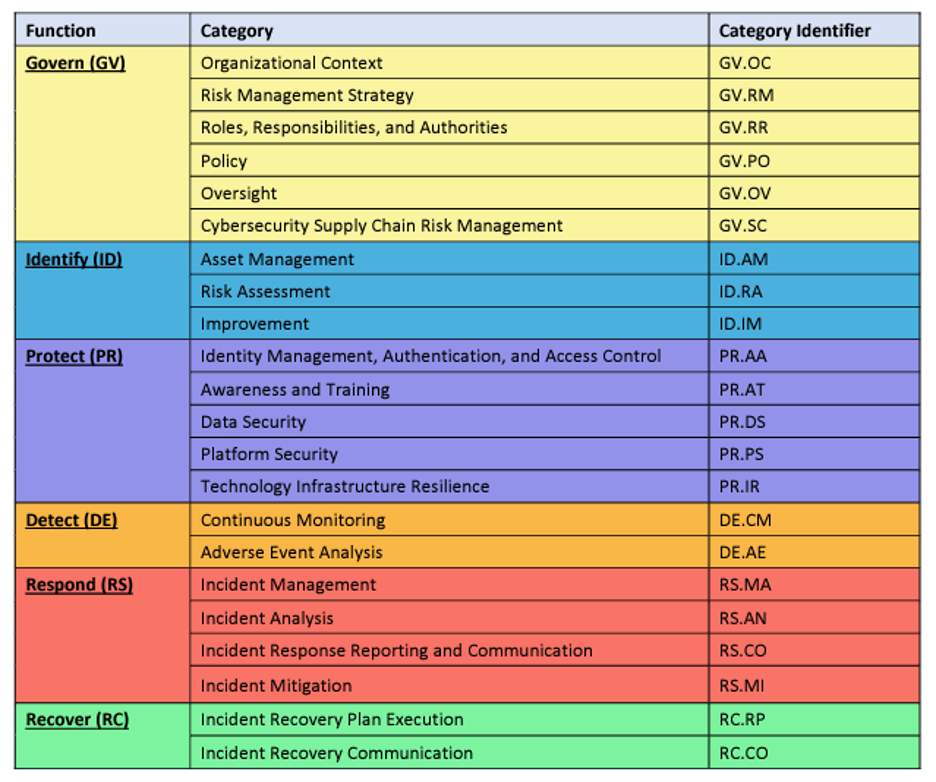
NIST CSF version 1.1 controls are organized into five (5) functions, which are then broken down into twenty-three (23) categories and one hundred and eight 108 subcategories. NIST CSF version 2.0 has twenty-two (22) categories and one hundred and six (106) subcategories. NIST CSF version 2.0 is organized into six (6) functions.
NIST CSF 2.0 includes additional guidance via informative references that can be used to provide direction on outcomes from established global standards, guidelines, frameworks, regulations, and policies.
Included with the publication of NIST CSF 2.0 is the Resource and Overview publication which summarizes the intentions of each Function as well as additional reference material for organizations aiming to integrate NIST CSF 2.0 into their cybersecurity and risk management programs:
This publication includes released resources such as the following:
- Informative References – view and create your mappings between CSF 2.0 and other documents.
- Cybersecurity & Privacy Reference Tool (CPRT) — A centralized and enhanced mechanism for managing reference datasets between NIST cybersecurity and privacy.
- Implementation Examples – examples of action-oriented steps to help achieve a category and subcategory objectives.
- CSF 2.0 Reference Tool – Human and machine-readable versions of the Core Functions.
NIST has also released various guides for organizations to consider and reference when integrating NIST CSF 2.0 into their cybersecurity and risk management programs:
- NIST CSF 2.0 Quick Start Guides (QSD):
Use this for:
Guidance for Organizational Profiles
Creating and Using CSF 2.0 Profiles and Community Profiles:
Aimed for groups of organizations with shared interests in cybersecurity risk management within a specific context, such as a sector, technology, or challenge. Use case-specific cybersecurity risk management guidance for multiple organizations.
- Current Profile: Describes the cybersecurity outcomes that an organization is currently achieving.
- Target Profile: Describe the outcomes an organization wishes to achieve to improve its cybersecurity risk management.
Small Business (SMB):
While it’s not intended to replace CSF, it guides small- to -medium sized businesses, non-profits, and schools in kick-starting cybersecurity risk management strategy.
Using the CSF Tiers:
Explanations on how to apply the CSF tiers alongside organizational profiles.
- Partial (Tier 1): Characterized by an ad-hoc and sometimes reactive approach to cybersecurity risk management.
- Risk-Informed (Tier 2): Risk management practices are approved by management but may not be established across the organization as policy.
- Repeatable (Tier 3): Risk management practices are formally approved and expressed as policy.
- Adaptive (Tier 4): The organization adapts its cybersecurity practices based on lessons learned and predictive indicators from previous activities.
Cybersecurity Supply Chain Risk Management (C-SCRM):
Helps organizations improve their C-SCRM processes.
Enterprise Risk Management (ERM):
Introduction to how ERM SMEs can utilize the outcomes within CSF 2.0 to improve risk management.
These informative references include multiple calls to the Cyber Risk Institute (CRI) Profile 2.0, which is now released as well. The CRI profile can be utilized for the ability to adapt and expand coverage of other topic areas that are relevant to cybersecurity. The CRI Profile is made for a by the financial services sector, the categories and associated subcategories are relevant to any sector.
At Tevora, we understand our clients’ priorities. We’ve developed customized reporting templates to help organizational leaders report accurate assessment results to their boards. With our expert guidance, technical reports, and insightful dashboards, we’ve helped organizations successfully evaluate their NIST CSF maturity year-over-year. Whether your organization is transitioning from CSF version 1.1 to CSF version 2.0, or implementing the newly released 2.0, allow us to navigate the resources, translate technical risk(s) into comprehensible business risk(s), create industry benchmarking and comparisons, and craft your CSF and cyber risk management strategy. Reach out to us today to discover how we can fortify your business’s security posture.
We Can Help
If you have questions or would like help with your certification, give us a call at (833) 292-1609 or email us at sales@tevora.com.