Apr 8, 2022
FFIEC & GLBA Risk Assessment and Maturity Services
What is the FFIEC?
The Federal Financial Institutions Examinations Council (FFIEC) is a joint interagency body of key federal financial agencies built to provide guidance and recommendations to promote uniformity in the supervision of financial institutions. The key players in the FFIEC are the Federal Reserve Board (FRB), the Federal Deposit Insurance Corporation (FDIC), the National Credit Union Administration (NCUA), the Office of the Comptroller of the Currency (OCC), and the Consumer Financial Protection Bureau (CFPB). The FFIEC was created to address and enforce several financial laws, regulations, and requirements passed by the members of the FFIEC and the federal government.
What is GLBA?
Gramm-Leach-Bliley Act (GLBA) is a federal law that requires “financial institutions” under FTC jurisdiction to implement the proper security controls to ensure the confidentiality, integrity, and availability of any customer or consumer information.
Do I need to comply with FFIEC or GLBA? Or Both?
The easiest determination if you need to comply with FFIEC or GLBA is to determine if your organization is a financial institution according to GLBA law. In addition, the FFIEC helps organizations meet the other regulatory compliance controls resulting from the federal agencies within the council. If you are subject to any of those agencies security requirements then the FFIEC tool can be used to help you meet the necessary compliance.
Am I a “Financial Institution”?
A financial institution is any institution any size, which are “significantly engaged” in providing financial products or service. Essentially, if your organization participates or has ownership interesting in an organization that conducts business activities or services that are financial in nature not limited to:
- Banking services (i.e. loans, check cashiers, exchanges)
- Depository institutions
- Insurance
- Investment management products
- Investment or financial advisory services
- Financial underwriting
- Tax preparation services
- Credit reporting
In its essence, if your organization’s services involve a financial transaction or service, your organization is subject to GLBA law and the FFIEC controls can help you identify and manage your cybersecurity risk.
Do I process Nonpublic Personal Information (NPI)?
Nonpublic Personal Information (NPI) is personal information about a consumer that is provided to obtain a financial product or service. As privacy laws continue to strengthen collection and protection requirements, financial institutions should understand that NPI goes beyond just financial information. To help understand what data NPI is exactly and how should it be protected, it can be split into two categories; individual information and financial information
Individual information is information specific to an individual and their identity. This information can clearly define who a person is or may be information a person would not want disclosed to the public. This can include:
- Name
- Address
- Telephone Number
- Social security number
- Passport Number
- Driver’s License
- Dates of Birth
Financial Information is specific financial information tied to a customer and their engagement to a financial institution. As such, this information if disclosed to:
- Customer Status (if they are active customer or not)
- Income
- Account Numbers
- Payment History
- Account Balances
- Purchase History
- Credit/Debit Card Numbers
Any component or combination of information about a customer or their financial dealing will classify as NPI. As a result, financial institutions are required by GLBA to implement security programs and controls to protect this information.
What am I required to do to meet GLBA?
GLBA requires financial institutions to build an information security and privacy program with relevant administrative, technical, and physical security controls based on a financial institution’s scope, technical environment, and the extend and depth of personal data is collected. Key objectives of the program include:
- Protecting the security and confidentiality of customer information
- Implementing protections against threats or hazards to the security and integrity of consumer information
- Securing access to and use of consumer information that results in the harm or inconvenience to any customer.
In an effort to support the development, implementation, and enforcement of the information security program, GLBA requires financial institutions to elect an individual to manage the program and get the financial institution’s management buy-in. In addition, a regular risk assessment must be conducted to assess the security risks and threats the organization faces, the effectiveness of security controls in place, and the mitigation measures for identified risks.
While many financial institutions are able to establish the required information security program and its essential safeguards, many financial institutions fail to capitalize on the key benefits for a robust, maturity cybersecurity program and controls.
FFIEC and GLBA
As an effort to help financial institutions meet GLBA requirements as well as other FFIEC security requirements, the FFIEC created the Cybersecurity Assessment Tool (CAT) to assist financial institutions conduct in-depth risk assessments to determine its cybersecurity risk and information security program maturity.
FFIEC CAT Tool
The CAT tool is broken out into two sections the inherent risk profile and maturity controls.
Inherent Risk Profile
The inherent risk profile assists financial institutions determine their inherent risk profile based on their business operations, technologies in place, how services are provided, and external threats the financial institution faces. After completing the inherent risk profile questions, the tool will automatically assign an inherent risk profile. This section is critical in determining what security controls financial institutions should have in place to secure its environment as well as identify gaps and areas of improvement. At the end of the inherent risk assessment, the financial institution will be assigned a risk level.
Least
This type of organization has a very minimal use of technology with a limited offering of products and services. This type of organization operates with a few employees and in a small geographic locations. Basic security controls are needed to protect this organization.
Minimal
This type of organization has a limited use of proven technologies with a lower-risk product and service offerings. This type of organization operates with a few employees and in a small geographic locations. Mission critical operations and systems are outsourced in this organization. Both baseline and evolving security controls are needed to provide additional controls to mitigate riskier operations or services.
Moderate
Moderate financial institutions have a moderate technology complexity with a higher offering of products and services that may be inherently higher risk. Similar to minimal, mission critical operations are outsourced but some internal hosting may be completed. A moderate maturity of security controls will be needed in order to mitigate cyber risk in this environment.
Significant
A Significant institution offers a higher risk products and services with the help of more complex and emerging technologies. A significant institution will have a large workforce, with contractors, operating in a large geographic locations. To support the business, the organization will use a substantial amount of devices and connections. Strong security controls and innovation is required to ensure the security of NPI in this environment.
Most
This type of organization uses cutting edge technology to deliver a large spread of high-risk products and services. The organization may outsource key operations but primarily hosts internal applications and systems. Overall, this organization requires innovative security controls to mitigate as much risk as possible.
Maturity Levels
The maturity level section captures how intricate and developed security controls that an organization implemented. there are five risk levels assigned to an organization. Financial institutions with higher inherent risk profiles should look to design and incorporate stronger maturity level controls. For example, a Moderate inherent risk institution should be operating at an evolving, intermediate, or advanced maturity level. To determine these levels, the FFIEC created the following diagram below.
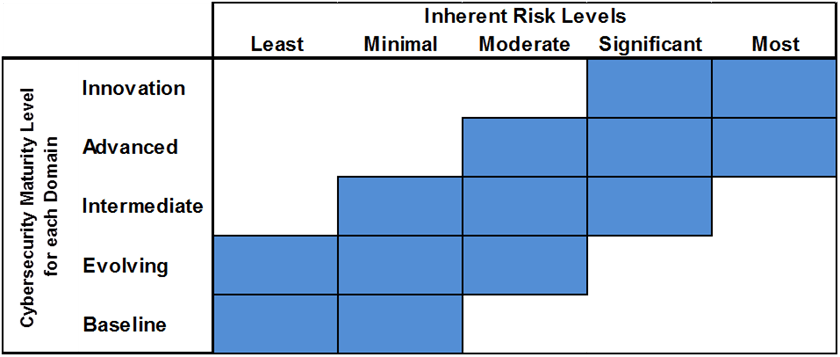
The maturity risk tab helps determine the security controls in place and whether or not a financial institution meets the expected maturity level. If an organization fails to meet those controls, that can be a significant risk to the organization.
The maturity risk evaluates controls based on the following five domains.
1. Cyber Risk Management and Oversight
This domain addresses the institutions ability to oversee and develop an effective enterprise cybersecurity program with key policies and procedures.
2. Threat Intelligence and Collaboration
This domain assesses a financial institutions ability to find, evaluate, and communicate relevant cyber threats to all stakeholders.
3. Cybersecurity Controls
This domain addresses a financial institutions current cybersecurity controls in place to protect itself and its customers.
4. External Dependency Management
This domain assesses a financial institutions ability to maintain a comprehensive third-party risk management program to evaluate and secure any third party relationships or connections properly.
5. Cyber Incident Management and Resilience
This domain addresses a financial institutions ability to identify, respond, mitigate, and report cyber security events and incidents. Additionally, this domain evaluates a financial institutions ability to maintain and recover business operations before, during, and after a cyber incident.
Each control within the CAT tool is assigned a maturity level:
Baseline- A baseline control is the minimum control expected to be in place to provide an organization a security foundation. These controls are typically dictated by law or regulations.
Evolving- An evolving control is providing an additional layer of documentation such as policies and procedures for security actions not required by law. Most of these controls help organizations establish a vital practices for a strong security culture and environment.
Intermediate- Intermediate control leverages detailed, and formalized processes that can be repeated on a regular basis. The formalization of these practices make the execution of cybersecurity practices easier to risk-based decisions.
Advanced- Advanced controls integrate analytics and automation into cybersecurity practices. Stronger accountability and execution responsibilities are assigned at this maturity level.
Innovative- Innovative controls drive cutting edge methods and technology into identification, treatment, and monitoring of cybersecurity risk. Predictive analytics and state-of-the art tools and processes are used to treat and manage risk.
Overall, the maturity assessment reviews 494 controls to determine a financial institution’s security profile and risk. If one control is not met for the maturity assessment, that subdomain maturity level is not met leaving your organization potentially susceptible to cyber risks and consequences such as disclosure of customer information that results in legal fines, loss of customer trust, and ultimately an impact on your bottom line.
Tevora Can Help
Phase 1- GLBA/ FFIEC Risk Assessment
Our unique approach for assessing your organization is derived from two standpoints. We identify risk from a process-based perspective and an asset-based perspective.
Process-Based Risk
We will evaluate the inherent risk and control effectiveness of your information security processes and programs to identify and prioritize risks. We provide recommendations within the report of process and program improvements to mitigate risk within your environment according to your risk tolerance.
Asset-Based
We will work with your organization to identify all of your assets and determine the inherent and residual risk of your assets and the applicable threats that they face. We are able to provide key threat scenario analysis with existing and emerging threats facing the financial industry. The recommendations for risk mitigation or compensating control the risk of these treat vectors will be included in the report.
Combined Report
This two-layer risk assessment approach ensures your organization efficiently identifies risk across your entire enterprise and ensure that you meets all compliance requirements according to GLBA and FFIEC. We use our unique HydraRisk model to evaluate and describe risks to your organization. We also are able to customize the assessment to meet your enterprise risk management programs and methodologies as well.
As for the execution of the assessment, Tevora will review your environment, documentation, and interview your staff to determine areas of information security risk in context of your institution’s inherent and residual risk profile. The risk assessment will be documented in a report that provides information and context to identified risks and recommendations for risk treatment. We provide our cybersecurity expertise to pinpoint areas of weakness and improvement to help secure your environment from a variety of emerging threats.
Not only do we provide key details on how you are reaching or failing to meet GLBA and FFIEC requirements but we provide insight and recommendations of improvement based on industry best practices and emerging threats, vulnerabilities, and risks trends.
Phase 2 – Remediation Support
Additional services that Tevora can provide involves our team providing hands-on implement support to help mitigate the risks identified. As the assessors, we have the unique opportunity to help your organization take action on the identified risk within the GLBA/FFIEC Risk Assessment.
Within the remediation process, Tevora can assist with:
- Information Security Program Development and Management
- We can help develop key policies and procedures to develop or support your organization’s information security program.
- Risk Management Program Development
- We can develop and customize a robust risk management program to identify, treat, and monitor risk effectively.
- Service Support
- Tevora can provide key cybersecurity services to further strengthen and determine cyber risk to your organization, such as penetration testing.
- Solution Implementation
- We help implement industry-leading security solutions to automate and safeguard your environment.
Phase 3- Security Roadmap
Tevora can help develop a strategic roadmap to help your organization effectively design and execute projects within your cybersecurity program. We will establish a realistic timeline for the methodical implementation of the milestones and goals set by your organization. The roadmap document will help determine key resource needs, projects, and recommendations to assist you in achieving an ideal state for your security program. As your institution grows and changes over time, your inherent risk profile may change resulting in emerging risk impacting your business operations. The roadmap plan will ensure that as your organization offers new products, sets up business in new locations, and grow its customer base, you are protecting your organization and your customers information. Additionally, the roadmap will help plan and design key initiatives to reach a higher state of maturity.
Additional Resources
Additional resources on the FFIEC and GLBA requirements:
- FFIEC Cybersecurity Assessment Tool
- FTC – Complying with the Safeguard Rule
- FTC- Complying with the Privacy Rule
- GLBA Law Text
Talk to an Expert
If you have questions about GLBA, FFIEC, or other risk and compliance needs, just give us a call at (833) 292-1609 or email us at sales@tevora.com.