Cloud Security & Compliance
Tevora Cloud Security Services
Cloud Security Architecture
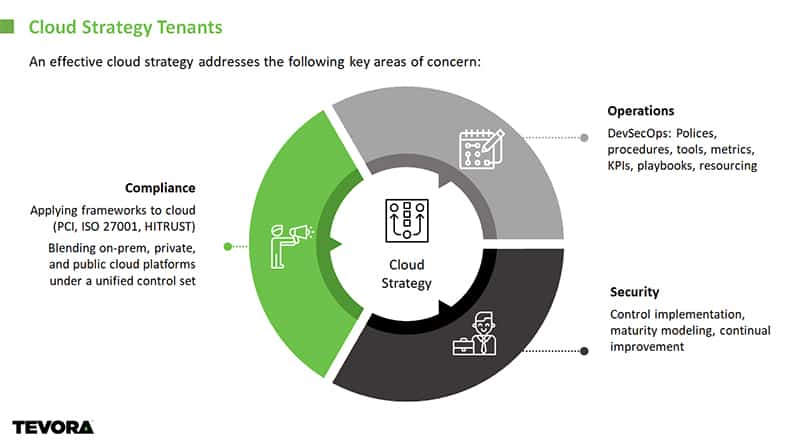
A move to the cloud is more than a simple “lift and shift” of your applications and services. Tevora applies architectural best practices for establishing, operating and continuously improving reliable, secure and efficient systems in the cloud.
Cloud Compliance
Tevora provides critical visibility into providers’ security controls, allowing for important assessments of those controls against your specific requirements for compliance. Automated security audits and compliance artifact creation assist in demonstrating ongoing compliance.
DevSecOps
Tevora’s use of DevSecOps ensures that security is part of the development process. This proactive approach to inserting security between development and operations ensures that the most current decisions regarding security can be incorporated, eliminating security gaps and compliance bottlenecks.
Cloud Security Automation
Technology evolves continuously, which means change is a constant in the cloud environment. Wherever possible, Tevora manages change through automation, leaving less room for human error and ensuring the secure, compliant deployment of cloud infrastructure and systems.
Our Expertise and Toolsets
The Tevora cloud team of specialists and engineers has deep expertise in public cloud infrastructures including:
- Amazon AWS
- Google Cloud
- Microsoft Azure
We rely on industry-leading toolsets for specific capabilities including:
- Compliance and control enforcement: Palo Alto, RedLock, EvidentIO
- Security automation and orchestration: Demisto
- Continuous security and compliance: Cloud Conformity
- Multi-cloud management, security and automation: HashiCorp
- PLUS: Our own proprietary tools written against cloud APIs