Jun 21, 2022
Why HITRUST™ i1 Certification Matters for Healthcare Vendors
Healthcare vendors are increasingly falling victim to ransomware, phishing, and other cyberattacks, putting sensitive health information at risk. Against this backdrop, the Provider Third Party Risk Management (PTPRM) Council—a leading industry watchdog for healthcare vendor security and risk management—has recently expanded its guidance to recommend that moderate risk vendors provide information security assurances through the HITRUST™ i1 certification process. The Council recommends this approach as being preferable to other less-stringent mechanisms.
In this blog post, we’ll provide background on HITRUST™ and PTPRM and unpack the new PTPRM guidance regarding HITRUST™ i1 certification.
What Is HITRUST™?
The HITRUST™ organization provides a framework that safeguards sensitive information and can help manage information risk for organizations across all industries. Its programs have been widely adopted in the healthcare industry.
Until recently, organizations wishing to obtain HITRUST certification have been required to undergo a rigorous HITRUST™ Common Security Framework (CSF) Validated Assessment performed by a third-party External Assessor organization that has been approved by HITRUST™ to perform validated assessments.
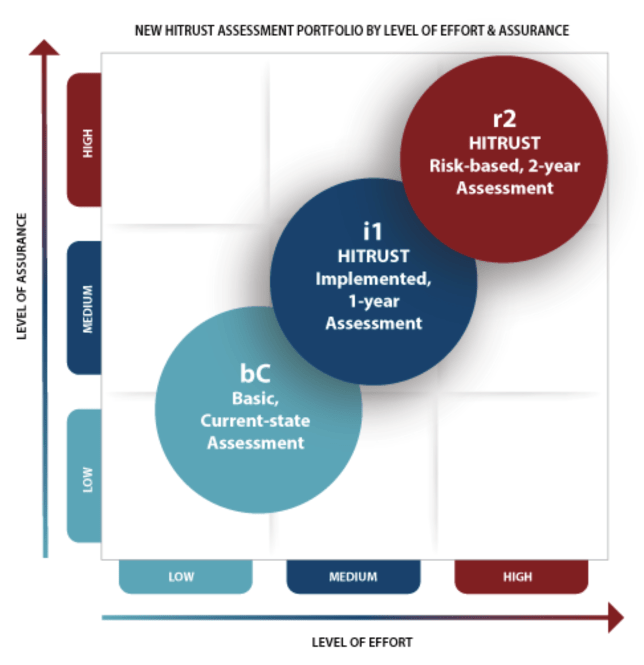
In October 2021, HITRUST™ announced two new assessment options to accommodate organizations with different levels of risk exposure. With these additions, HITRUST™ now offers three assessment alternatives:
- The Basic, Current-State (bC) Assessment (New). Suitable for lower-risk scenarios. Offers higher reliability than self-assessments and questionnaires. Uses HITRUST™ Alliance Intelligence Engine—an Artificial Intelligence (AI) tool—to identify errors, omissions, and deceit.
- The Implemented, 1-Year (i1) Validated Assessment (New). Suitable for moderate-risk scenarios or where a baseline risk assessment is needed. HITRUST™ Authorized External Assessors will validate i1 Validated Assessments.
- Risk-Based, 2-Year(r2) Validated Assessment (Current). This is the new name for the CSF Validated Assessment. Otherwise, the requirements are the same. Suitable for higher-risk scenarios. HITRUST™ Authorized External Assessors will validate r2 Validated Assessments.
What Are The Main Attributes Of i1 Assessments?
HITRUST provides the following description of i1 Assessment attributes:
“By using 219 pre-set control requirements[1] that leverage security best practices, ongoing threat intelligence data, and the MITRE ATT&CK Framework, the i1 keeps pace with the latest cyberattack threats, including ransomware and phishing.
- Moves security assessments beyond a check-list model to a more dynamic approach that ensures control selection is continuously relevant in defending against the latest threats and cyberattack techniques.
- Designed to sunset controls that have lost relevance and have limited assurance value.
- Focuses on Implementation for greater assurance that control requirements are in place and operating as intended.
- Uses the proven HITRUST CSF framework, which is highly prescriptive and constantly updated, unlike many other frameworks that are vague and remain unchanged for years.
- Assessment and testing through a highly qualified HITRUST Authorized External Assessor firm of your choice and the comprehensive HITRUST QA process for Validation and Certification (if earned).
- Leverages good security hygiene and leading practices that substantially cover authoritative sources, such as: NIST SP 800-171, HIPAA Security Rule, GLBA Safeguards Rule, U.S.Department of Labor EBSA Cybersecurity Program Best Practices, Health Industry Cybersecurity Practices (HICP).
- 1-year Certification, which can help justify reductions in cyber insurance premiums.
- Reduces time, effort, and cost by Inheriting prior assessment results along with reliance on sharing cloud controls.
- Leverages the HITRUST Results Distribution System (RDS) online portal to share assurance reports with relying parties through a PDF, web browser, and/or API so they can obtain, interpret, and analyze assessments more efficiently.
- Since some organizations choose an i1 Assessment based on speed-to-completion considerations, HITRUST has established a 45 business days (or less) post-submission Service Level Agreement to complete QA on Validated i1 Assessments—or the customer’s next i1 Validated Assessment report credit is free. (Note: Validated assessment submissions that enter escalated QA due to quality concerns are exempted from this SLA.)”
How Does The i1 Fit Into The Full HITRUST Assessment Portfolio?
As depicted below, the i1 Assessment fits in the middle of the HITRUST assessment portfolio and is intended for organizations that require a medium level of assurance and a medium level of effort:
What Is PTPRM?
The PTPRM Council is comprised of Prominent Chief Information Security Officers (CISOs) from leading health systems and provider organizations, including:
- Allegheny Health Network
- Cleveland Clinic
- University of Rochester Medical Center
- UPMC
- Tufts Medicine
- Shriner’s Hospitals for Children
- Mayo Clinic
PTPRM’s mission is to develop, recommend, and promote practices that enable health systems and providers to effectively manage information security-related risks in their supply chain and safeguard patient safety and information.
What Is PTPRM’s Guidance Regarding HITRUST™ i1 Certification?
PTPRM recently expanded its guidance to address certification recommendations for moderate-risk health vendors. Previously, PTPRM had only provided guidance for high-risk vendors that handled Protected Health Information (PHI).
The PTPRM Council now recommends that moderate risk vendors handling Personally Identifiable Information (PII) and other confidential information obtain HITRUST i1 certification. The Council recommends this approach as being preferable to other assurance mechanisms such as a SOC2 report. They list several benefits of the i1 certification approach, including:
- Ensures suitability of controls, transparency, and quality of assessment findings.
- Addresses relevant threats without putting an excessive burden on the certifying vendors.
- Ensures that vendors are effectively managing breach-related risks.
What Steps Should We Take To Achieve HITRUST™ i1 Certification?
Tevora has helped many of the world’s leading healthcare organizations achieve HITRUST certification, and we’ve developed a proven, cost-effective approach. Tactical and precise, the road to HITRUST certification with Tevora is a simple three-step process:
Gap Analysis
- We perform a tactical gap analysis to identify areas where your environment falls short of HITRUST requirements.
- We work with you to create a direct and focused remediation plan for achieving HITRUST compliance.
Remediation
- We help you prepare for your certification in an organized, efficient manner.
- We jump in to help you with anything from writing security policies to implementing controls.
Validated Assessment
- As a HITRUST Authorized External Assessor, we are fully qualified to perform the recently-announced i1 Validated Assessment.
We would love to be your trusted partner in this process, but if you prefer to do it on your own, we’d recommend using a similar approach. Keep in mind that you will still need to partner with a third-party HITRUST Authorized External Auditor to perform the i1 Validated Assessment.
Additional Resources
Below are additional resources that provide a deeper dive on the topics covered in this blog post:
- PTPRM Council Website
- HITRUST Announcement of i1 Assessment + Certification
- Tevora Blog: HITRUST Offers Streamlined Assessment Alternatives for Healthcare Organizations
We Can Help
If you have questions about HITRUST i1 certification or would like help bringing your organization into compliance, our team of experienced HITRUST and healthcare security experts can help. Just give us a call at (833) 292-1609 or email us at sales@tevora.com.
[1] A HITRUST i1 Validated Assessment performed using the HITRUST CSF v9.6 framework includes 219 control requirements, however to address emerging cyberthreats in the future, the number of requirements included in i1 assessments may change over time. To ensure the i1 Assessment requirement selection remains up-to-date, HITRUST evaluates security controls and reviews threat intelligence data no less than quarterly, and for each release of the HITRUST CSF framework.