Creating A Comprehensive Penetration Testing Program

Since launching Tevora’s penetration testing practice in 2003, it has become one of our largest and most successful service offerings. We do several hundred engagements a year for organizations of all sizes. In this blog post, we’ll leverage our learnings over the last 19 years to help you create a comprehensive penetration testing program for your organization.
What Makes a Successful Penetration Testing Program?
There are two key ingredients for developing a successful penetration testing program:
- Implement a continually evolving process for identifying and remediating potential attack vectors and improving cyber response certainty.
- Focus on raising the floor for possible attacks.
While it’s reasonable to be able to identify and remediate vulnerabilities to known threats, you’ll also need to be able to effectively respond to unknown—zero-day—threats. As we like to say, “zero days can happen to anybody.” And you can’t prevent all attacks. So, you need to ensure you can identify new advanced threats when they occur and have a plan, processes, tools, and people in place to quickly diagnose and remediate these threats. An effective penetration testing program will continually evolve to help your team prepare for and respond to known and unknown threats.
A good penetration testing program also will increase your certainty about the details of an attack, including:
- Is it really an attack or just an anomalous but harmless event?
- What happened initially?
- What’s happening now?
- What systems, networks, and business functions are impacted?
- Is it an isolated event or an ongoing threat?
Having certainty about the details of an attack is critical for rapid remediation.
Finally, a successful penetration testing program will help you raise the floor for possible attacks. While it’s virtually impossible to protect your environment against all threats (e.g., sophisticated attacks initiated by state actors), you can do a lot to reduce your vulnerability to most types of attacks. For example, you can raise the floor significantly by using penetration testing to fortifying your defenses against relatively basic and opportunistic threats such as ransomware and phishing attacks, which have become increasingly common in the last few years.
What’s the Purpose of a Penetration Testing Program
We feel there are three main reasons for having a penetration testing program:
- Identify unknown attack vectors. You probably suspect that some aspects of your environment are vulnerable to certain kinds of attacks. But what about the attacks that you don’t know about? Penetration testing can help you identify those potentially dangerous unknown attack vectors.
- Validate suspected attack vectors. Clients often suspect they have certain vulnerabilities. Penetration testing will usually reveal that some of these areas are actually not vulnerable, while validating that others represent significant risks. This allows you to focus your efforts on the real threats.
- Manage Risks. Executive management and Boards often think in terms of risks to the organization. Penetration testing helps you identify the risks introduced by vulnerabilities in your environment and quantify them based on potential impact and likelihood of occurrence. This information is essential for determining whether specific risks should be mitigated, transferred to a third party, or accepted. It’s also a great way to gain buy-in and management support for funding security improvements.
Is Penetration Testing the Same as Vulnerability Scanning?
Many cybersecurity firms claim vulnerability scanning is the same thing as penetration testing. We beg to differ. While vulnerability scanning has a place in an overall penetration testing program, you need to conduct penetration testing to determine if potential vulnerabilities identified in vulnerability scans can actually be exploited. Without demonstrating exploitation, you can’t have that level of certainty we discussed earlier.
What Are Key Things We Should Consider When Building a Penetration Testing Program?
So, you’re sold on creating or enhancing a penetration testing program for your organization. But you want to know what are the key things you should consider in doing this. Here’s our take.
Complexity
Complexity is the single biggest cybersecurity problem. If you don’t fully understand your cybersecurity solutions, or have solutions that are too complicated for your people to manage effectively, you may have too much complexity. Our view is that you should carefully assess how much complexity you need in your organization to address your risks. Key factors in determining this are:
- Size. How big is your organization, and how much data do you have that could be of value to attackers?
- Risk. How much risk can you tolerate? If your business is flipping burgers, you may be able to tolerate a fair amount of risk. If you handle state secrets and weapon systems, your risk tolerance is likely going to be lower.
- Access and Opportunity. What access and opportunities for exploitation exist within your environment?
Balancing Spend With Risk
Once you have a good understanding of your risks, you can adjust your cybersecurity spend to match your level of risk, targeting the sweet spot depicted below.
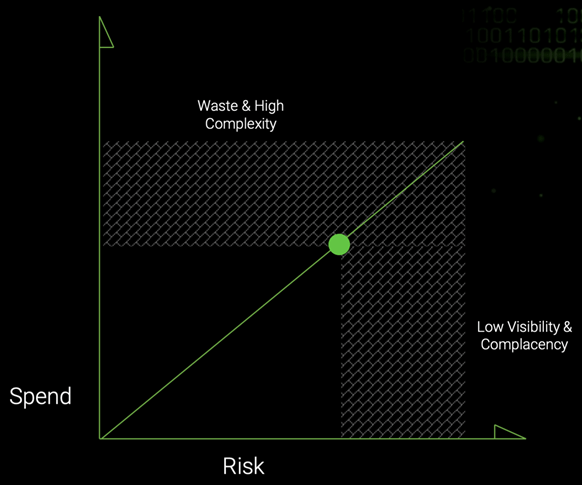
If you find yourself in the bottom right portion of this chart, consider increasing your cybersecurity spend to meet your level of risk. If you are in the top left portion, you likely have too much complexity and waste and should consider reducing your cybersecurity spend to match your risk.
What Goals Should We Have for Our Penetration Testing Program?
We recommend that your penetration testing program focus on three goals: validating attack vectors, identifying application vulnerabilities, and assessing control efficacy. Here are the areas we suggest targeting within each of these goals:
Validate Attack Vectors
- Vulnerability exploitation
- Code execution
- Establishing command and control
- Lateral movement
- Data exfiltration
Identify Application Vulnerabilities
- Form/field logic
- Input validation
- Authentication enforcement
- Authorization enforcement
- Vendor trust/supply chain security
Assess Control Efficacy
- Identification of Indicators of Attack/Compromise
- This includes tools, processes, standards, and personnel
What Types of Testing Should Be Included in Our Penetration Testing Program?
To some extent, the types of penetration testing that should be included in your program will be dependent on your specific business and technical environment and the level of risk you can tolerate. Below we’ve provided a list of the types of penetration testing to consider when developing a program, starting with fundamental tests and moving on to more mature tests.
Fundamental-measures the susceptibility of an environment to attack
- Network (internal or external)
- Web application, API, mobile, rich application
- Cloud
- Wireless
- Embedded device
- Code review
- Social engineering-phishing and phone protecting
- Physical
- Atomic Red Team-using Red Canary toolset to programmatically execute multiple attack scenarios
Mature-more advanced tests to measure fundamental areas as well as personnel and security control efficacy
- Red Team-covert attack simulation; no holds barred
- Purple Team-joint exercise with penetration test team and first responders
How Often Should We Conduct Penetration Tests?
We recommend conducting your full complement of penetration tests at least once a year. This testing should include external, internal, and cloud testing. Consider running some tests more frequently if you have areas that you feel are especially vulnerable or if you become aware of emerging attack vectors that represent a high level of risk for your organization.
What Are the Most Effective Ways to Prepare for Penetration Testing?
In our experience working with clients, there are a few relatively basic things you can do in advance of penetration testing that will significantly reduce the number of vulnerabilities found in the testing.
- System and Network Segmentation. For example, if you are in the restaurant business, putting your credit card data on a separate system and network segment goes a long way towards reducing the vulnerability of this sensitive data to attacks. Be sure to enforce segmentation at OSI stack layers two, three, four, and seven.
- Two-Factor Authentication (2FA). Enforce 2FA everywhere, with no exceptions. In our penetration testing, we often are able to gain access to systems by exploiting exceptions when they exist. This means no more grandfathered service accounts or waiving 2FA requirements for key executives. Enforcing 2FA across the board may cause some initial grumbling from your team, but you just need to bite the bullet and do it.
Webinar
For a deeper dive on this topic, check out our Creating a Comprehensive Penetration Testing Program webinar.
Additional Resources
Here are some additional Tevora resources that expand on areas covered in this blog post.
- How Cloud Penetration Testing Can Help You Defend Against 3 Common Attack Vectors
- Understanding PCI Penetration Testing and Vulnerability Scanning Requirements
- Leveraging Attack Simulation to Up Your Incident Response Game
- Red Teaming with Physical Penetration Testing and Social Engineering
- Red Team Attack Simulation Datasheet
- Internet of Things (IoT) Penetration Testing Datasheet
- Application Penetration Testing Datasheet
Talk to an Expert
If you have questions about creating or enhancing a penetration testing program, or would like help implementing one in your environment, just give us a call at (833) 292-1609 or email us at sales@tevora.com.
About Tevora
Founded in 2003, Tevora is a specialized management consultancy focused on cybersecurity, risk and compliance services. Based in Irvine, CA, our experienced consultants are devoted to supporting the CISO in protecting their organization’s digital assets. We make it our responsibility to ensure the CISO has the tools and guidance they need to build their departments, so they can prevent and respond to daily threats.
Our expert advisors take the time to learn about each organization’s unique pressures and challenges, so we can help identify and execute the best solutions for each case. We take a hands-on approach to each new partnership, and –year after year –apply our cumulative learnings to continually strengthen the company’s digital defenses.